4 Real-life RBAC Use Cases in 2024 & How to Implement Them?
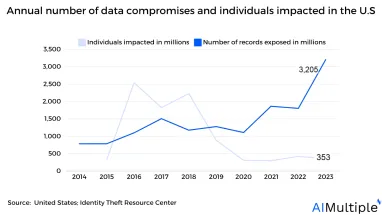
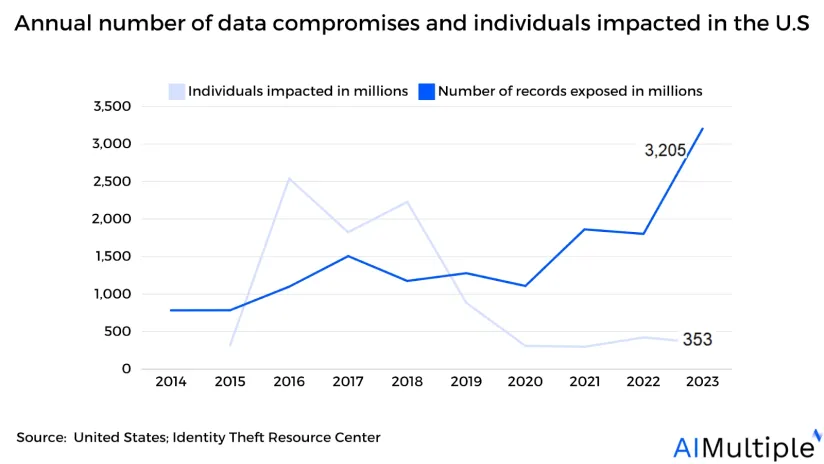
Source: Identity Theft Resource Center1
Network security statistics show that in 2023, 3,205 data compromises were reported, and data intrusions such as breaches, leaks, and exposure harmed over 353 million people in the U.S. While they are two distinct incidents, they have one thing in common. All two occurrences result in an unauthorized threat actor gaining access to sensitive data.
Organizations can use open source RBAC and microsegmentation tools to build a more granular and secure network for intrusion prevention. This article discusses the top 4 RBAC use cases with real-life examples, and how to implement them.
4 Real-life use cases of role-based access control (RBAC)
We will look at real-life RBAC examples from large corporations with 500+ employees and small-scale businesses while examining how they set role-based network security policies to protect their systems.
1- Assigning roles and permissions on corporate databases
1.1 CVS Pharmacy
CVS Pharmacy is an American retail company. CVS sells prescription drugs and a wide array of common merchandise, including over-the-counter drugs, beauty products, and cosmetics through their CVS Pharmacy and Longs Drugs retail stores, and online through CVS.com.
Designing scopes for CVS Pharmacy with REST APIs: To implement the RBAC system for CVS Pharmacy, administrators should create scopes that correlate to REST APIs. Scopes are permissions that specify the level of access a certain role has to each API endpoint.
Table 1: Scopes for the following REST APIs
| Categories API | Drugs API | Customers API | Orders API |
|---|---|---|---|
| create:categories: POST /categories | create:drugs: POST /drugs | list:customers: GET /customers | create:orders: POST /orders |
| write:categories: PUT /categories/:id | write:drugs: PUT /drugs/:id | write:customers: PUT /customers/:id | list:orders: GET /orders |
| delete:categories: DELETE /categories/:id | delete:drugs: DELETE /drugs/:id | delete:customers: DELETE /customers/:id | read:orders: GET /orders/:id |
| list:categories: GET /categories | list:drugs: GET /drugs | read:customers: GET /customers/:id | write:orders: PUT /orders/:id |
| read:drugs: GET /drugs/:id |
Allocating scopes to roles: After stating the scopes for each REST API, the administrator can allocate them to the relevant user roles by drag-and-drop options or writing queries in the CVS Pharmacy ecosystem. In this specific example, by using the “GRANT SHOW ON DATABASE categories TO ROLE store_admin;” administrators may grant a role (read: categories) to a user group (store_admin).
Table 2: Allocation of scopes to the CVS Pharmacy functional business units
| Scopes | Guest | Customer | Store admin | Store manager | Customer service | 3PLs | Marketing specialists |
|---|---|---|---|---|---|---|---|
| create:categories | ✅ | ✅ | |||||
| write:categories | ✅ | ✅ | |||||
| delete:categories | ✅ | ✅ | |||||
| list:categories | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| create:drugs | ✅ | ✅ | |||||
| write:drugs | ✅ | ✅ | |||||
| delete:drugs | ✅ | ✅ | |||||
| list:drugs | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| read:drugs | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ |
| list:customers | ✅ | ✅ | |||||
| write:customers | ✅ | ||||||
| delete:customers | ✅ | ||||||
| read:customers | ✅ | ✅ | |||||
| create:orders | ✅ | ✅ | ✅ | ✅ | ✅ | ✅ | |
| list:orders | ✅ | ||||||
| read:orders | ✅ | ✅ | |||||
| write:orders | ✅ |
Note: ✅ Means that the functional business unit can access the CVS Health resources based on the REST constraints.
1.2 Costco Wholesale
Costco Wholesale is an American multinational business that maintains a network of membership-only big-box warehouse club retail locations. The company deals with a massive amount of confidential customer information. Using RBAC is critical for protecting sensitive customer data and retaining customer loyalty. For example, Costco Wholesale can define roles, responsibilities, and permissions for the functional departments in its value chain such as:
Role: Order fulfillment
- Responsibilities: Processing and shipping orders placed by customers.
- Permissions: Access to order information, customer profiles, inventory management, and shipment logistics.
Role: Financial analyst
- Responsibilities: Analyzing financial data and creating reports.
- Permissions: Access to financial databases and order information.
Role: Customer service agent
- Responsibilities: Assisting customers with queries and difficulties.
- Permissions: Access to customer profiles and order information for support reasons.
Table 3: Allocation of scopes to the Costco functional business units
| Scopes | Order fulfillment | Financial analyst | Customer service | |
|---|---|---|---|---|
| Order information | ✅ | ✅ | ✅ | |
| Customer profiles | ✅ | ✅ | ||
| Inventory management | ✅ | |||
| Shipment logistics | ✅ | |||
| Financial databases | ✅ |
2- Assigning roles and permissions for small businesses
Dental office
Consider a dental office that subscribes to a software-as-a-service (SaaS) product to administer, and promote healthcare services to potential customers with the following modules:
- A billing module that collects payments from insurance companies and patients for medical services covered by dental billing codes.
- A sales module that enables dental settings to categorize potential leads according to their likelihood of purchasing a product and service from your organization.
The dental office administrators may use your software’s user interface (see Figure 2) to assign permission access to various business functions. By using drag-and-drop options administrators can use your software to create different permissions such as “view” “edit” “create” and delete”.
Across the billing module administrators can assign specific rules stating that only the “billing manager” will have a permit to view billing codes, customer ID, and create invoices.
- view: billing_codes
- view: customer_ID
- create: invoice
Similarly, administrators can set permissions for the sales module users such as:
- view: sales_database
- create: sales_database
- edit: sales_database
- delete: sales_database
After setting permissions the administrator can create a “sales manager” role and assign these permissions to that role, limiting other employee’s access to the sales database.
Figure 2: Assessing RBAC policies for the “sales_manager” with user interface (UI) elements

These role-to-permission mappings change slowly and may be recorded in static mapping by using an open policy agent (OPA), open-source, general-purpose policy engine, to define an authorization policy. These mappings can be saved in a data.json file and packed with the policy.
Figure 3: Example of how the data.json file may look for the “billing_manager” and the “sales_manager” roles:

Read more: Network security poly management, network security policy management solutions.
RBAC use cases with datasets and queries
At the query level, administrators may create individual queries for each role permissions.
3- Setting network access permissions
Administrators can allow access exclusively to user groups within the business network such as “AWS VDPC”. Consider a network rule that restricts access using private endpoint identifiers such as AWS VPCE IDs that do not affect public network accesses. Network administrators can construct two different role-based network rules to restrict access based on “private endpoint IDs” while entirely blocking requests from “public IPv4 addresses”.
The following network rules might be integrated into a network policy to enable private AWS IDs while limiting public network traffic.
Figure 4: Allowing access exclusively to users within the business network “AWS VDPC”

4- Defining user and case-specific access permissions:
Administrators can use RBAC to allow applications access only during work hours for chosen roles. For example, assume the administrator wants to build a query that states only the users in the sales department can modify CRM records during working hours.
In this example, it is supposed that the setting that our policy will examine has a dynamic characteristic, such as the time of day. We’ll specify a list of permissible hours of the day and days of the week in a data.JSON file that will follow the role-based access policy (assuming that time is updated in real-time in the CRM database).
Figure 5: Allowing access only during work hours for a specific application and role with data.JSON queries

What is RBAC?
Role Based Access Control (RBAC) is a role-based approach to granular access control, in which users are assigned one or more roles with varying permissions.
Figure 1: RBAC system workflow

Source: Okera2
Note: Microsegmentation can also bring granular access controls to your organization. To learn more read the top 10 microsegmentation tools.
Why use RBAC?
Unauthorized network access accounts for 40% of third-party cyber intrusions that occurred in 2023.3Considering that unauthorized access is one of the main drivers of data breaches, establishing RBAC is critical, especially for companies with several employees.
For example, in a freight forwarding company area distribution managers, export specialists, and pricing managers may all need to use the same CRM software, but their level of authority required across the system will be different. At this point, RBAC can help determine the required degree of access for all users performing a certain job function and allocate those users to a role using the appropriate set of permissions. With RBAC IT professionals may add, alter, and delete rights for all users in a group at once, and change the access level of a particular user by assigning or deleting a role.
Read more: Mandatory access control (MAC).
How do you implement RBAC in your organization?
1. Create inventory systems
Make a detailed inventory of all servers, databases, applications, external websites, and other resources that users may require access to. Include physical security in this list as an option, which would encompass access to servers or other key physical areas and resources. Make a map showing who (or what) presently has access to those resources.
2. Establish business workflows
Determine who will interact with them and how:
- Identify the specific resources that various users require to complete their tasks and map internal procedures.
- Decide whether to allow authorization inheritance between roles or require separation of tasks.
- Analyze whether to construct roles that are consistent with existing usage or to employ newly defined roles.
For example,
- Consider an application that allows travel nurses to submit invoices for travel expenditures and receive reimbursement.
- The travel nurse sends an inquiry about their reimbursement claim.
- The healthcare manager evaluates the inquiry and either accepts, or denies it. If the request is approved, the reimbursement will be handled.
- The financial accounting team conducts audits to ensure they are following internal policies.
Meanwhile, when a travel nurse sends an invoice, a new cell is added to the invoice table, and a new pending status is generated in the accounting system. Thus, the healthcare manager may then examine submissions and change the status attribute. Separately, the financial accounting staff will have access to all submissions for auditing.
In this case, the healthcare managers need to evaluate the invoice inquiries sent from travel nurses, therefore they require access to travel nurse IDs. However, the financial accounting team requires lower-level access. Thus, the company may create role-based access control policies that offer higher-level authority to the healthcare manager, such that that the healthcare manager will inherit the permissions of the financial accounting team, for example:
- Healthcare manager can access, travel nurse IDs, and invoice submissions
- Financial accounting team can access all invoice submissions but not travel nurse IDs.
Disclaimer: This is a basic example to illustrate how a business workflow can relate to RBAC controls, organizations need to build more complex query-based internal maps defining each user’s roles.
3. Create roles based on your business functions
Predefined roles examples may include:
Power User: Manages the model creation and execution process. This job provides high-level access to many functional domains. Power Users can conduct all of the same tasks as regular users. Furthermore, a Power User can accomplish these tasks:
- Creates ad hoc layouts, and loads data employing the data integration system.
- Manipulates data.
- Develops and executes integrations.
- Builds models.
User: Users can execute all of the same things as Viewers. A User can do the following extra operations:
- Performs ad hoc tasks, but cannot write back into ad hoc layouts or load data using the data Integration system.
- Creates, changes, and deletes rules
- Executes and deletes reports.
Viewer: Can only see and evaluate data; cannot write to it. A Viewer conducts the following operations:
- View models.
Note: Predefined roles are hierarchical. Higher-level roles inherit the access given by positions at the lower levels. Power users inherit privileges provided through the User, and Viewer roles in addition to their own.
4. Audit regularly
Perform periodic network audit practices to ensure that users are allocated to the right roles (since roles might change over time) and that each position has the necessary permissions. Don’t make one-time alterations to accommodate one employee’s specific demands. Either change their position’s permissions or establish a new role if needed.
Read more: Network security audit tools.
For guidance on choosing the right tool or service, check out our data-driven sources: network security policy management (NSPM) tools and incident response tools.
Further reading
- Top 10 Microsegmentation Tools
- Intrusion Prevention: How does it work? & 3 Methods
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
- Cybersecurity Risk Management
AIMultiple can assist your organization in finding the right vendor.
External Links
- 1. ”Identity Theft Resource Center 2023 Annual Data Breach Report“. Identity Theft Resource Center. January 25, 2024. Retrieved April 29, 2024.
- 2. ”Role-Based Access Control (RBAC)”. Okera. 2023. Retrieved April 29, 2024.
- 3. ”BLACK KITE 2023 THIRD PARTY DATA BREACH REPORT“. BLACK KITE. January 31, 2024. Retrieved April 29, 2024.

Cem is the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per Similarweb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Sources:
AIMultiple.com Traffic Analytics, Ranking & Audience, Similarweb.
Why Microsoft, IBM, and Google Are Ramping up Efforts on AI Ethics, Business Insider.
Microsoft invests $1 billion in OpenAI to pursue artificial intelligence that’s smarter than we are, Washington Post.
Data management barriers to AI success, Deloitte.
Empowering AI Leadership: AI C-Suite Toolkit, World Economic Forum.
Science, Research and Innovation Performance of the EU, European Commission.
Public-sector digitization: The trillion-dollar challenge, McKinsey & Company.
Hypatos gets $11.8M for a deep learning approach to document processing, TechCrunch.
We got an exclusive look at the pitch deck AI startup Hypatos used to raise $11 million, Business Insider.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on

Comments
Your email address will not be published. All fields are required.