Identify New Technologies
Accelerate Your Enterprise
Join the 6 million business users confidently choosing new tech. Leverage focused, data-driven insights from reviews, case studies, and more to quickly discover the right solutions for your business

Trending Research Studies on AIMultiple
Top 100+ Generative AI Applications / Use Cases in 2024
Large Language Model Evaluation in 2024: 5 Methods
Top 10 AI Chip Makers of 2024: In-depth Guide
Discover Research Studies
Enterprise Generative AI: 10+ Use Cases & Best Practices for Enterprises in 2024
Generative AI, also called GenAI, presents novel opportunities for enterprises compared to middle-market companies or startups including: However, generative AI is a new technology with unique challenges for enterprises: Executives wonder how their organizations can reap the benefits of generative AI while overcoming these challenges.

Compare Top 20+ AI Governance Tools: A Vendor Benchmark in '24
According to AI stats, 90% of commercial apps are expected to leverage AI by the end of 2025. Despite the increasing role of AI, business leaders are concerned due to: One recent answer to this problem is the adoption of AI governance tools (See Google Trends Graph). These tools can help deliver ethical and responsible AI.
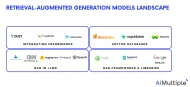
12 Retrieval Augmented Generation (RAG) Tools / Software in '24
Generative AI stats show that Gen AI tools and models like (ChatGPT) can automate knowledge intensive NLP tasks that make up 60% to 70% of employees’ time. Yet, 56% of business leaders consider AI-generated content biased or inaccurate, lowering the adoption rate of LLMs.

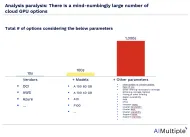
Top 10 Cloud GPU Providers in 2024
GPU procurement complexity has been increasing with more providers offering GPU cloud options. AIMultiple analyzed GPU cloud providers across most relevant dimensions to facilitate cloud GPU procurement. While listing pros and cons for each provider, we relied on user reviews on G2, other online reviews as well as our assessment.
Cloud GPUs for Deep Learning: Availability& Price / Performance
If you are flexible about the GPU model, identify the most cost-effective cloud GPU If you prefer a specific model (e.g. A100), identify the GPU cloud providers offering it. If undecided between on-prem and the cloud, explore whether to buy or rent GPUs on the cloud.
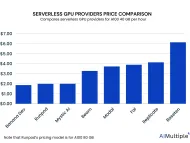
Top 10 Serverless GPUs: A comprehensive vendor selection in '24
Large language models (LLMs) like chatGPT has been a hot topic for business world since last year. Thus, the number of these models have drastically increased. Yet, one major LLM challenge prevents more enterprises adopting it, system costs for developing these models.

Comparing 10+ LLMOps Tools: A Comprehensive Vendor Benchmark
The number of large language models (LLMs) has been increasing since 2019 due to the models’ extensive application areas and capabilities (See Figure 1). Yet, the estimates show that designing a new foundation model can cost up to $90 million while fine-tuning or enhancing existing large language models can cost $1 million to $100 thousand.

LLMOPs vs MLOPs in 2024: Discover the Best Choice for You
In the rapidly evolving landscape of artificial intelligence and machine learning, new terminologies and concepts frequently emerge, often causing confusion among business leaders, IT analysts, and decision-makers. Among these, two terms have gained prominence: LLMOps vs MLOps.

Top 7 Generative AI Services & Vendors in 2024
After the launch of OpenAI’s ChatGPT, generative AI technology started to grow rapidly across industries. Generative AI tools work by using deep learning techniques to create new data instances similar to the input data, giving human creativity to AI. The technology has paved the way for diverse applications in various industries and areas (Figure 1).

Top 100+ RPA Use Cases/Projects/Examples in 2024
RPA can be used to automate repetitive tasks in the front office and back office. Some common sectors using RPA include: In this article, we will explore RPA use cases in 5 buckets: Disclaimer Our list of use cases is comprehensive, but not exhaustive.
Stay ahead of the curve
1 free email per week with the latest B2B tech news & expert insights to accelerate your enterprise.