10 Cybersecurity Best Practices for Enterprises in 2024
Organizations are vulnerable to the most common cyber attack vectors, and the numbers agree since cyberattacks rose 30% in 2022.
Companies need to improve their cybersecurity risk management posture before they lose money and reputation due to a successful breach (see Figure 1). This article introduces the top 10 cybersecurity best practices for executives to improve their firms’ cybersecurity posture.
Figure 1: Cost of successful cyberattacks:
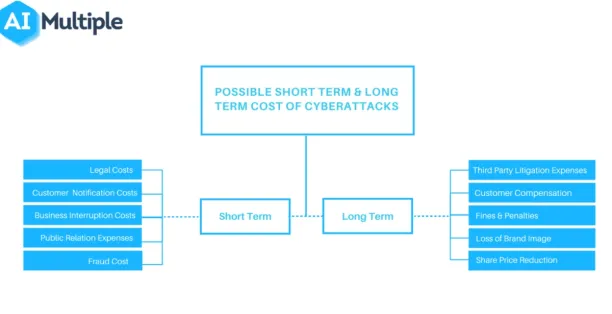
Long and short-term costs of cyberattacks
1. Adopt suitable technology to reach zero trust principles
Some technologies support a zero-trust mentality. Companies can deploy the following technologies to improve their cybersecurity posture:
- Data loss prevention: With the rising number of data breaches, employing automated Data Loss Prevention or DLP software has become crucial for protecting your business’s sensitive information. Additionally, automated DLP systems can significantly reduce the workload on IT departments by efficiently monitoring, detecting, and responding to potential threats without constant human oversight.
- Secure access service edge (SASE): SASE is the unified network and security solution for organizations that have network and security components together. SASE’s network as a service component includes SD-WAN, carriers, content distribution networks, and edge devices. Security as service components include firewall as a service, ZTNA, and SWG.
- Zero trust network access (ZTNA): ZTNA is a cybersecurity solution that constantly verifies users and devices to permit access.
- Secure web gateway (SWG): SWG provides protection against internet-based cyber threats thanks to functions like URL filtering and malicious code detection.
- Software defined perimeter (SDP): SDP software is the new generation network cloaking tool. Unlike VPN, it allows microsegmentation and ensures the least access privilege.
- Firewall audits: Automated firewall audit software can enhance a company’s network security by systematically identifying and rectifying configuration errors and vulnerabilities.
2. Prepare board and C-level leaders
Without board and C-level leadership buy-in and oversight, it is almost always impossible for firms to transform. The cybersecurity posture of a company is not an exception. The board needs to demonstrate a high maturity about cybersecurity concerns where they have at least basic knowledge about:
- Cost of cyber threats.
- Types of cyber attacks.
- Industry-related cyber weaknesses.
- Compliance measures.
- Recent cybersecurity posture of the company.
- Available technologies.
In a company that has an effective organizational structure, board and C-level leaders should have the following duties:
- C-level cybersecurity leaders: The board must appoint a C-level leader, such as a chief information security officer (CISO), to be responsible for the company’s cybersecurity management. This person should be knowledgeable about both the business and technological aspects of the issue.
- Regular cybersecurity meetings: Cyberattacks and their results must be regularly shared with the board. However, according to the “2021 cybersecurity breaches” survey, almost one-third of companies do not inform the board.
- Board-departments collaboration: The company’s cybersecurity policy must be disclosed to the board. Departments and boards of directors must work up a budget for system maintenance and new technology investment. However, almost 70% of companies do not take such actions.
- Third-party assurance: Firms must work with third parties to ensure their progress.
- Targeting international certificates: Board must consider having international certifications like ISO 27001 or HIPAA that represent data compliance of companies. Targeting such certificates help firms to improve their cybersecurity posture.
3. Determine your current cybersecurity posture
Prioritization is critical for introducing a successful transformation plan. Firms must begin improving their cybersecurity posture by minimizing the greatest risk instruments. Consider your firm and the data where attackers are most likely to strike.
Would they be interested in personal information about your employees or your customer databases or intellectual property? Make a list of the most likely targets. Consider the regulations you must meet and your current measures for protecting employee and customer intellectual property data. For example, in March 2022, the US Congress passed a bill requiring firms in vital sectors (finance, transportation, and energy) to report cyberattacks and data breaches immediately to defend national infrastructure.
After finding these weak points, you can search for ways that mitigate these risks.
4. Enhance employees’ cybersecurity awareness
Almost half of the business leaders think personal mistakes are the primary cause of a data leak at their company. The rise of remote/hybrid working expands the scope of employee-caused data breaches, as mobile workers frequently use insecure computers and Wi-Fi networks, making them easy targets for hackers.
Therefore, educating employees regarding the following issues is an important cybersecurity best practice:
- Pop-ups, unknown emails, and links: Phishing and hacking people by sending some links or pop-ups are frequent types of cyberattacks. Fraudsters try to steal information from employees by sending them official-looking emails. Employees of all levels should receive regular cybersecurity awareness training to help them become better at recognizing phishing emails, fake websites, bogus, and other signs of fraud.
- Passwords: Fraudsters have sophisticated methods for cracking passwords, and it is relatively simple for them to do so, especially if your password contains your name or date of birth. A password should be at least 12 characters long and have a combination of numbers, symbols, and upper- and lower-case letters. Firms should, however, utilize multi-factor authentication for added protection, as we outline in best practices #4.
- Wi-Fi security: Cybercriminals can utilize wireless sniffing software to reach data and transactions when employees use public access points that are not secured. Thus, employees should not use public Wi-Fi, especially when they work with sensitive data.
- Software updates and patches: Only 43% of corporations have a commitment of installing software upgrades within 14 days. On the other hand, businesses can protect themselves against cyber dangers by updating software. Thus, they should educate their employees on the need for updating.
- Regular virus monitoring: Employees often use their own laptops or devices due to remote/hybrid working. However, they might not have antivirus programs or they might not use them regularly. Thus malware software can cause data breaches.
5. Implement zero trust cybersecurity paradigm
According to the zero trust cybersecurity paradigm, potential users, devices, and network systems are always verified to gain access to documents. Thus, it is a suitable cybersecurity best practice in today’s hybrid/remote working practices where the device and network security is ambiguous.
- Introduce multi-factor authentication: Cyber attacks often use hacked accounts to gain access to a firm’s internal resources. Multi-factor authentication makes it difficult for hackers to access corporate data.
- Validating devices: Device identity and security, in addition to user identification, should be validated systematically.
- Minimize data access: Allowing employees access to as little data as they need to complete tasks (least access privilege) reduces the attack surface and, thus, the cost of successful breaches.
- Adopt micro-segmentation: To prevent computer viruses from spreading quickly (lateral movement), data should be stored in numerous micro-segments.
6. Conduct API security testing
90% of developers rely on APIs to enhance their services efficiency and customer friendliness; however, only 11% of businesses have an API security plan that covers testing APIs in its entirety. That is why it is not surprising that 95% of APIs experienced security exploits in 2020. vulnerable API can be exploited by:
API security testing can:
- Protect from external attacks.
- Identify security flaws in the code before API deployment.
- Comply with security regulations.
- Report potential risks to the API in real-time.
Sponsored
PULSE is an automated AI-based testing tool provided by Testifi. PULSE can reduce the cost and effort of testing by 50%. Major companies such as Amazon and BMW use their services.
7. Employ white hat hackers
Measurements are always necessary to assess the performance of your measures. Therefore, it is logical to employ white hat hackers who examine your cybersecurity without causing any data leakages.
White hat hackers (also known as ethical hackers) utilize their hacking expertise to find security flaws in infrastructure, software, and networks. White hat hackers do not violate the law and do not cause data breaches, unlike black hat hackers.
To examine the performance of your cybersecurity posture, white hat hackers use the following methods:
- Email phishing.
- Denial-of-service (DoS) attack.
- Pen testing.
- Implement social tests within the company to assess workers’ weaknesses.
8. Implement audit trails in your digital operations
Audit trails are used to bring robustness to operations in cases such as:
- Lowering the risk of fraud
- Preventing significant errors in financial statements
- Preventing unauthorized users from accessing company resources
- Assisting businesses in identifying attempts at asset theft
Similarly, they are useful in cybersecurity in providing the data to figure out how security incidents happen.
The key to responding to unanticipated situations quickly is a timely investigation of the behaviors or movements of your staff, privileged users, or third-party vendors. An audit trail can benefit your company by:
- Enhance the responsiveness to incidents by preparing security teams to learn from past incidents to better prepare for future security incidents by reconstructing events via audit trail analysis
- Aiding security personnel in spotting instances where hackers attempt to breach networks and do harm.
- Detecting cyberattackers’ previously hidden activity
- Preventing negative actions like system abuse and internal fraud
9. Back up your critical data
At its core, cybersecurity management is concerned with minimizing the reputational and financial consequences of cyberattacks. Consequently, businesses should consider not only preventing data breaches but also minimizing the cost of successful breaches.
Ransomware assaults, which seize business data and release it in exchange for a random amount of money, more than doubled in 2021. If the leaked documents are critical to the company’s core activities, the corporation becomes heavily dependent on hackers. As a result, routinely versioning key data and keeping it in a separate location (hardware, for example) might help businesses stay operational following a ransomware attack.
10. Purchase cybersecurity insurance
As we digitize, new risks, such as cybersecurity risks, emerge. Thus, the insurance sector finds new instruments that reduce an entity’s risks. Cybersecurity insurance minimizes the damages of cyberattacks. As of the beginning of 2022, almost 70% of companies use such policies.
Cybersecurity insurance provides coverage for the following scenarios:
- Privacy liability coverage: Covers against legal costs and penalties
- Network business interruption cost: Covers expenses during a period when they are unable to function as a result of a cyberattack.
- Media liability coverage: Covers reputational costs of cyberattacks.
You can also check our cybersecurity software and cybersecurity services lists.
If you need further assistance regarding cybersecurity, please contact us:

Cem is the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per Similarweb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Sources:
AIMultiple.com Traffic Analytics, Ranking & Audience, Similarweb.
Why Microsoft, IBM, and Google Are Ramping up Efforts on AI Ethics, Business Insider.
Microsoft invests $1 billion in OpenAI to pursue artificial intelligence that’s smarter than we are, Washington Post.
Data management barriers to AI success, Deloitte.
Empowering AI Leadership: AI C-Suite Toolkit, World Economic Forum.
Science, Research and Innovation Performance of the EU, European Commission.
Public-sector digitization: The trillion-dollar challenge, McKinsey & Company.
Hypatos gets $11.8M for a deep learning approach to document processing, TechCrunch.
We got an exclusive look at the pitch deck AI startup Hypatos used to raise $11 million, Business Insider.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on
Comments
Your email address will not be published. All fields are required.