Top 10 IAST Tools in 2024 Based on 300 Users' Experiences
Securing applications against evolving security threats is crucial for protecting sensitive data and functionality. Traditional methods like Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST) offer valuable insights but have limitations. Interactive Application Security Testing (IAST) combines static analysis to identify vulnerabilities and capabilities of DAST tools to perform security checks in a runtime environment.
Emerging IAST tools help secure the software development lifecycle. AIMultiple identified the top tools based on key benefits, analysis capabilities, and how they fit with your existing security stack.
IAST Tools Comparison
| Vendor | Ratings with reviews* | Employees | Free Trial | Focus |
|---|---|---|---|---|
| Invicti | 4.6 from 60+ reviews | 300+ | ✅ (for 15 days) | Web apps |
| Synopsys Seeker | 4.3 from 100+ reviews | 10,000+ | ❌ | Web apps |
| Acunetix by Invicti | 4.2 from 90+ reviews | 300+ | ❌ | Web apps |
| HCL AppScan | 4.1 from 70+ reviews | 4,000+ | ✅ | Web apps |
| Contrast Assess | 4.5 from 40+ reviews | 300+ | ✅ | Web apps |
| Checkmarx One | 4.2 from 30+ reviews | 500+ | ❌ | Web apps |
| OpenText Fortify On Demand | 3.9 from 20+ reviews | 20,000+ | ✅ | Web apps |
| PT Application Inspector | 200+ | ❌ | Web apps | |
| NowSecure | 4.6 from 20+ reviews | 100+ | ✅ | Native mobile apps |
| eShard esChecker | 40+ | ❌ | Native mobile apps |
* All ratings are out of 5
Vendors are sorted by focus and number of reviews, with the exception of sponsors. Sponsors have links and are listed at the top.
To choose the top IAST tools, AIMultiple relied on:
- The software reviews from reputable B2B review platforms like G2. 1
- The number of employees as they serve as a proxy for the companies’ revenues. The company should have at least 30 employees.
IAST Tools Differentiating Features
| Vendor | Is DAST/SAST also included? | Integrations with SIEM tools | Number of Supported Coding Languages* | Deployment options |
|---|---|---|---|---|
| Invicti | DAST + IAST | Splunk | 4+ | On-Prem, Cloud, Hybrid |
| Synopsys Seeker | IAST | 14+ | On-Prem, Cloud, Hybrid | |
| Acunetix by Invicti | DAST+ IAST | Splunk | 4+ | On-Prem, Cloud, Hybrid |
| HCL AppScan | SAST + DAST + IAST | IBM Security, QRadar | 30+ | On-Prem, Cloud, Hybrid |
| Contrast Assess | SAST + DAST + IAST | Azure Sentinel, Datadog, Splunk, Sumo Logic | 16+ | On-Prem, Cloud, Hybrid |
| Checkmarx One | SAST + DAST + IAST | Splunk | 20+ | On-Prem, Cloud, Hybrid |
| OpenText Fortify On Demand | SAST + DAST + IAST | 33+ | Cloud | |
| PT Application Inspector | SAST + DAST + IAST | 14+ | ||
| NowSecure | SAST + DAST + IAST | 6+ | On-Prem, Cloud | |
| eShard esChecker | SAST + DAST + IAST |
*To see each language in detail, refer to our table below.
IAST Tools Supported Coding Languages
| Software | Supported Coding Language |
|---|---|
| Invicti | .NET, PHP, Java, and Node.js |
| Synopsys Seeker | ASP.NET, C#, Clojure, ColdFusion, Go, Gosu, Groovy, Java, Node.js and
more
|
| Acutenix | JavaScript, PHP, JAVA, and .NET |
| HCL Software | SAP, ABAP,JavaScript Python, Node JS, C & C++ and more |
| Contrast Assess | Java, Ruby, Go, JS, .NET, Node JS, and more |
| Checkmarx One | Java, Python, C/C++, JavaScript, PHP, Go, Apex, |
| Open Text Fortify On Demand | ABAP/BSP, ActionScript, Apex, ASP.NET, C# (. NET), C/ C++, Classic
ASP (with VBScript), COBOL, ColdFusion, and more
|
| PT Application Inspector | Java, PHP, C#, Visual Basic .NET, JavaScript, TypeScript, Python, Kotlin,
Go, C/C++, Objective-C, Swift, SQL (T-SQL, PL/SQL, MySQL)
|
| NowSecure | Java, Kotlin, Swift, Objective-C C/C++, JavaScript |
| eShard esChecker |
Top IAST tools examined
Invicti
Invicti AppSec emphasizes its “ZeroNoise” approach, aiming to minimize false positives through machine learning and expert-curated rules. It offers comprehensive security testing capabilities, encompassing both static and dynamic analysis as an automated test runner.

Invicti, formerly known as Netsparker IAST, consolidates with existing workflows and addresses critical security areas like the OWASP Top 10 and compliance standards. 2 This combination of features and a wide range of programming languages, both web and server-side language compliance, makes Invicti a compelling solution for organizations seeking to elevate their application security analysis without sacrificing development efficiency.
Security focus:
Invicti’s primary focus is providing comprehensive application security, covering various aspects:
- OWASP Top 10: Identifies and mitigates vulnerabilities listed in the OWASP Top 10, a well-known list of critical web application security risks.
- Compliance standards: Helps meet compliance requirements for regulations like PCI DSS, HIPAA, and GDPR.
- API security: Secures APIs alongside web applications for holistic security coverage.
Point to consider
- Invicti and Acunetix, both web application security offerings by Invicti Security, diverge in their target audiences and functionalities. While both utilize advanced vulnerability scanning technology with automated verification, Invicti caters to larger enterprises, emphasizing integration and automation. Conversely, Acunetix targets smaller organizations preferring a more hands-on approach to security.
Contrast Assess by Contrast Security
Contrast Assess combined approach utilizing static, dynamic, and interactive analysis techniques in QA testing to further enhance its versatility. 3 Its strength lies in its extensive support for various programming languages, allowing it to scan code written in Java, Python, Node.js, and many others. This multi-pronged strategy leads to minimizing false positives, risk prioritization, and remediation guidance ensuring developers focus on identified vulnerabilities.
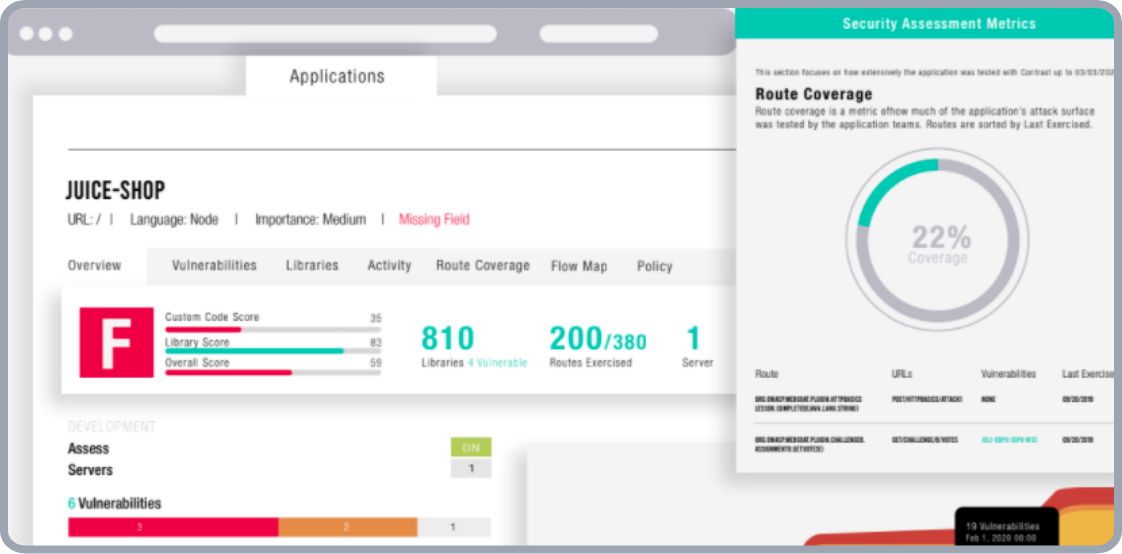
Point to consider
- Learning curve: Some users report a steeper learning curve due to the tool’s complexity, especially for teams new to application security testing. This might necessitate additional training and familiarization to fully leverage its capabilities in software composition analysis. 4
Checkmarx One™
While Checkmarx One offers features like multi-language support, integrated analysis types, and streamlined developer workflow, it’s crucial to consider potential drawbacks like cost, complexity, and false positives. This balanced analysis empowers you to decide if Checkmarx One aligns with your specific needs and avoid a one-sided approach. 5
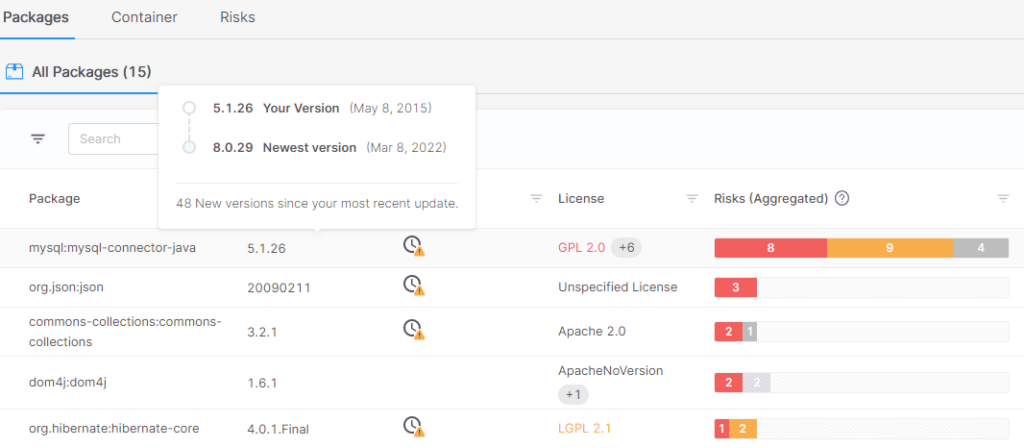
Security focus
Checkmarx One focuses on identifying and mitigating a wide range of application security vulnerabilities, including OWASP Top 10 vulnerabilities, injection flaws, broken authentication, and more. It also offers features like security risk scoring and prioritization to help developers focus on the most critical issues.
Points to consider
- Complexity: Some users note that Checkmarx One might have a steeper learning curve compared to simpler IAST tools. 6
IAST: Real-time vulnerability monitoring in the development process
IAST empowers developers by shifting security testing left in the SDLC, identifies vulnerabilities during the test/QA stage, and reduces remediation costs and delays. This aims to put developers in control and allows for continuous security testing throughout the software development life cycle by integrating with CI/CD pipelines.
Unlike other application testing tools, IAST provides immediate vulnerability reports after code changes, enabling developers to identify and fix vulnerabilities earlier in development. This integration, ease of use, and scalability make IAST a preferable option for web application development teams and DevOps environments to monitor vulnerabilities in the development cycle.
Offerings and limitations of IAST tools
Interactive application security testing (IAST) combines static analysis of source code with dynamic application security testing (DAST) techniques to perform penetration testing. Such comprehensive application security solutions are tailored for web application attacks in continuous testing environments.
| SAST | DAST | IAST | |
|---|---|---|---|
| Ideal For | -Complex applications with extensive and diverse codebases. -Early-stage development and continuous integration environments | -Web applications, APIs, and services. -Final stages of development, pre-release, and post-deployment security assessments | -Early vulnerability detection. -Lower false positive rate |
| Limitations | -False positives and negatives. -Detecting runtime and environment specific issues. -Identifying issues in third-party libraries and components | -Vulnerabilities that are detectable at runtime. -Requires a fully functional and deployed application. -Static code issues and deeply embedded vulnerabilities | -Initial setup and configuration |
Benefits
- Insights: IAST tools can identify real-time insights, enable early vulnerability detection (during testing/QA) and can detect up to 30% more vulnerabilities than traditional SAST methods, according to a 2024 Gartner study. 7
- False positivity reduction: By leveraging application logic and context Interactive Application Security Testing (IAST) provides accurate results with low false positives (compared to DAST and SAST). Most IAST tools’ automated testing capabilities generate up to 70% reduction, observed in a 2023 Forrester report. 8
Weaknesses
- Monitoring: One downside of IAST tools is that they are limited to identifying the vulnerabilities in the functional testing environment; they can not monitor security issues in areas of missing code coverage.
- Customizability: An important consideration is to maintain the balance between pre-configured rules and human tester control since the selected tool might have limitations in customizability.
How to complement IAST tools?
IAST tools can be complemented with DAST tools or SAST tools. For those starting their application security journey or working at SMEs, these can also be good starting points:
SAST vs. DAST vs. IAST tools
| Feature | SAST* | DAST** | IAST*** |
|---|---|---|---|
| Definition | -Source code analysis, -Byte code or binary code, -Identifies security vulnerabilities without executing the code. | -Testing an application from the outside in its running state.
-Used to find vulnerabilities that an attacker could exploit. | -Combines elements of both static and dynamic analysis. -Implemented as agents within the test environment to observe application behavior and report issues. |
| Approach – Testing Environment | -White-box testing approach, -Internal structure and design of the application are known and analyzed. | -Black-box testing approach. -Production-like staging environment stimulates external attacks. | -White-box testing approach. -Used in development, QA, or staging environments, -Application behavior observation. |
| Detection Method | -Detects security breaches, -Ensures compliance with security standards, -Analyzing source code before deployment using static analysis. | -Simulated attacks on a running application, -Penetration testing with automated tools. | -Application behavior and data flow in real-time monitoring, -Knowledge of the code structure from static analysis and dynamic testing identify vulnerabilities. |
| Detection of Vulnerabilities | -Syntax and semantic errors, -Insecure coding patterns, -Buffer overflows, -Injection flaws, -Cross-site scripting (XSS), -Improper error handling in the coding stage. | -Vulnerabilities that can be detected from outside the application, -SQL injection, -Cross-site scripting (XSS), -Vulnerabilities that an attacker could exploit after deployment. | -Runtime issues (like DAST), -Issues in the source code (like SAST). |
| Implementation | -Early in the development lifecycle, -During coding and integration phases. | -Later in the development cycle, -During testing phases after deployment in a staging or similar environment. -Requires no access to the source code. | -Requires integration with the application runtime environment. |
| Ease of Use | -Deployed in early-stage development, -Continuous Integration (CI) pipeline. | -Easier to set up and requires less configuration, -No need to access source code. | -Observing the application behavior in run-time, -Minimizes false positives. |
*SAST: Static Application Security Testing
**DAST: Dynamic Application Security Testing
***IAST: Interactive Application Security Testing
External links:
- 1. “Best Interactive Application Security Testing (IAST) Software in 2024“Retrieved on March 15, 2024.
- 2. “OWASP Top Ten “Retrieved on March 15, 2024.
- 3. “Contrast Assess“Retrieved on March 15, 2024.
- 4. “Contrast Security Reviews 2024: Details, Pricing, & Features | G2“Retrieved on March 15, 2024.
- 5. “Reducing Friction in AppSec Program Adoption: How Checkmarx One Can Help “Retrieved on March 15, 2024.
- 6. “Pros and Cons of Checkmarx 2024 “Retrieved on March 15, 2024.
- 7. “2024 Gartner study “Retrieved on March 15, 2024.
- 8. “Forrester“Retrieved on March 15, 2024.

Cem is the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per Similarweb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Sources:
AIMultiple.com Traffic Analytics, Ranking & Audience, Similarweb.
Why Microsoft, IBM, and Google Are Ramping up Efforts on AI Ethics, Business Insider.
Microsoft invests $1 billion in OpenAI to pursue artificial intelligence that’s smarter than we are, Washington Post.
Data management barriers to AI success, Deloitte.
Empowering AI Leadership: AI C-Suite Toolkit, World Economic Forum.
Science, Research and Innovation Performance of the EU, European Commission.
Public-sector digitization: The trillion-dollar challenge, McKinsey & Company.
Hypatos gets $11.8M for a deep learning approach to document processing, TechCrunch.
We got an exclusive look at the pitch deck AI startup Hypatos used to raise $11 million, Business Insider.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on
Comments
Your email address will not be published. All fields are required.