Top 5 Kaspersky Alternatives in 2024 With 11K+ User Reviews
Kaspersky is headquartered in Moscow, Russia, and offers cybersecurity software with a focus on endpoint protection against ransomware, malware, and vulnerabilities that lead to data loss and breach.
In 2017, the U.S. Security Department of Homeland Security banned Kaspersky products due to their alleged ties to Russian security services. In order to combat such allegations, the company made its source code open for verification.1
This article offers a comparison of top 5 alternatives to Kaspersky based on user reviews, ratings, prices, and features, including MDM, full-disk encryption, and more.
5 Kaspersky Endpoint Security Cloud Pro alternatives comparison
This section compares alternatives to Kaspersky Endpoint Security Cloud Pro in light of insights based on user reviews, user ratings, price, and software features.
Comparative table based on market presence and pricing
| Software product | # of reviews* | Rating* | Price** | Multi-OS | Deployment (on-prem&cloud) |
|---|---|---|---|---|---|
| Kaspersky Endpoint Security Cloud Pro | 317 | 4.3 | $437 | ✅ | cloud based |
| Trellix Endpoint Security | 3,571 | 4.3 | n/a | ✅ | ✅ |
| Symantec Endpoint Security Complete | 3,178 | 4.4 | n/a | ✅ | ✅ |
| CrowdStrike Falcon Endpoint Protection Pro | 1,957 | 4.8 | $500 | ✅ | cloud based |
| Eset Protect Complete | 1,170 | 4.6 | $288 | ✅ | cloud based |
| WeBroot Business Endpoint Protection | 1,001 | 4.3 | $150 | Windows&macOS | cloud based |
* Based on the total number of reviews and average ratings (on a 5-point scale) from Gartner, G2, Capterra, and TrustRadius software review platforms as of April 3, 2024.
** The price entails 5 devices/users per year. Other licensing terms, such as the minimum quantity of licenses needed, are not taken into account; features and prices are in accordance with the selected tiers/packages.
Comparative table based on features
| Software product | FDE | Device control | MDM | Web&email protection | MFA |
|---|---|---|---|---|---|
| Kaspersky Endpoint Security Cloud Pro | ✅ | ✅ | ✅ | ✅ | ❌ |
| Trellix Endpoint Security | ✅ | integrated TrellixePO | integrated TrellixePO | ✅ | integrated TrellixePO |
| Symantec Endpoint Security Complete | integration with Symantec DLP | ✅ | ✅ | ✅ | integration Symantec Validation & ID Protection |
| CrowdStrike Falcon Endpoint Protection Pro | ❌ | ❌ | ❌ | ❌ | integrated with Falcon Identity Protection |
| Eset Protect Complete | ✅ | ❌ | ❌ | ✅ | add-on |
| WeBroot Business Endpoint Protection | ✅ | ✅ | ✅ | ✅ | ❌ |
Notes
- The table was created from publicly available and verifiable data.
- The vendors are ranked based on the total number of reviews, with Kaspersky ranked at the top and sponsors following it.
- Transparency statement: Vendors with links to their websites are sponsors of AIMultiple.
To present an objective assessment of vendors, we took into account verifiable information from the public, like the number of reviews and user ratings on software review portals.
Vendor selection criteria
- Number of reviews: We included vendors with more than 300 total user reviews.
- Average rating: Above 4/5 rating on average across all software review platforms.
- Price: Selected software products vary in price, and publicly available prices of products are added to the table. Potential users can compare products according to their price and pricing drivers.
- Pricing driver: The price of products depends on multiple aspects, such as minimum licensing or admin user quantity, device quantity, or domain quantity. Businesses can choose between pricing driver options in accordance with the quantity and admin user.
Common features
We selected the vendors that deliver malware protection and USB control features.
Differentiating features
- Integration with operating systems: Requirements regarding operating systems. Multi-OS compatibility includes support for Windows, MacOS, and Linux based systems.
- Deployment: Includes cloud-based and on-premises options.
- Full-disk encryption (FDE): Encrypting the entire storage on endpoints. For more endpoint encryption
- Device control: Management of devices such as USBs, printers, and Blueetooth devşces via established consoles offered in product features. For more on comparative table based on device control features
- Mobile device management (MDM): Device control and management with a focus on mobile devices such as tablets, smartphones, laptops, and more.
- Web & email protection: Protecting data against leakage on web and email, with a focus on security measures against phishing attacks.
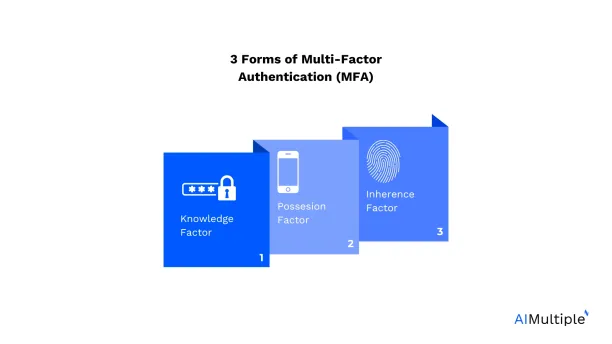
- Multi-factor authentication (MFA): Multi-factor authentication (MFA) is a security mechanism that requires multiple forms of verification from independent categories of credentials to authenticate a user’s identity. The purpose of multi-factor authentication is to provide an extra layer of security beyond just a username and password, which are susceptible to being stolen or guessed.
Kaspersky Endpoint Security Cloud Pro’s shortcomings
Reviewers have identified the following flaws, which have been raised multiple times:
1. Resource intensity
Multiple reviewers mention the program occupies storage space and lags the system.2 3 4
2. User interface and experience
The user interface has been found to be complicated by multiple reviewers. In addition, navigation on the console has been claimed to be cumbersome.5 6 7
Figure 1. User review on TrustRadius
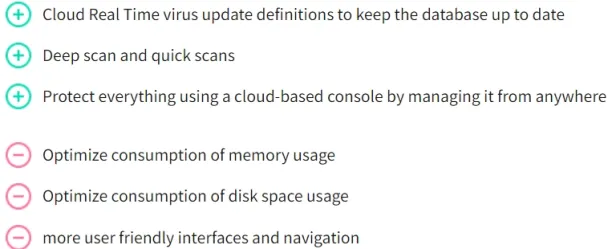
Source: TrustRadius.8
Top 5 alternatives analyzed
This section provides a user-reviewed analysis from sites such as G2, Gartner, Capterra, and TrustRadius. Pros and cons from user reviews are only chosen if several users bring up the same issue.
1. Trellix Endpoint Security
Trellix offers its clients extended endpoint detection and security (XDR) together with data, network, and email security. Bryan Palma, the COO and president of BlackBerry, is currently the company’s CEO.
Pros
- Threat prevention: Multiple reviewers are satisfied with the product’s threat prevention tools, including AV and malware detection.9 10
Cons
2. Symantec Endpoint Security Complete
The Symantec brand, which provides a range of hardware and software choices, is owned by Broadcom, Inc. Symantec offers cybersecurity products for server and endpoint security.
Pros
Cons
Figure 2. Symantec Endpoint Security Complete vs Trellix Endpoint Security (ENS)
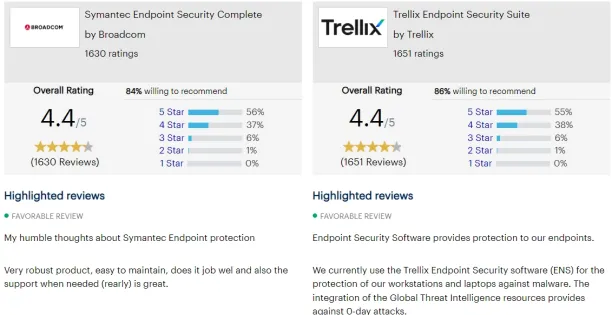
Source: Gartner.17
3. CrowdStrike Falcon Endpoint Protection Pro
Falcon by CrowdStrike is an endpoint protection platform that offers endpoint detection and response, exposure management, identity threat detection & response, IT automation, threat intelligence & hunting, cloud security, next-gen SIEM, generative AI, data protection, and workflow automation.
Pros
- Endpoint visibility: Multiple users claimed to be content with the product’s endpoint monitoring capabilities.18 19
Cons
Figure 3. Falcon Endpoint Protection platform features
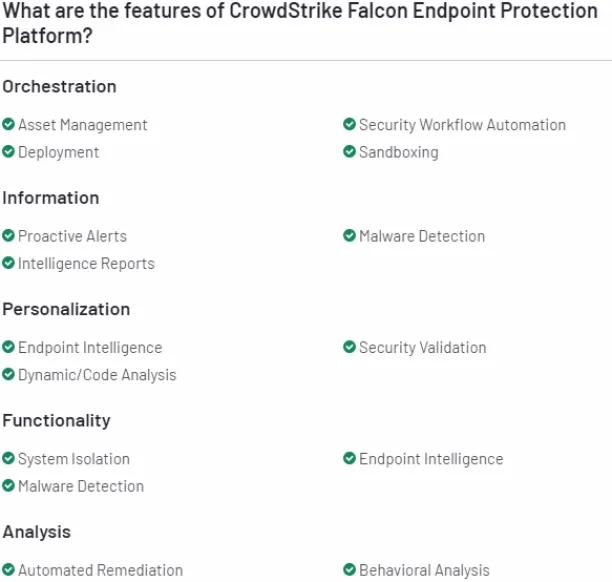
Source: G2.22
4. Eset Protect Complete
Eset was founded in Bratislava, Slovakia, in 1992. The company provides endpoint protection focused on zero-day threats, ransomware with a scope across web and cloud based applications.
Pros
- Endpoint security: Multiple users are satisfied with the product’s endpoint security capabilities, supported by malware protection and device control.23 24
Cons
Figure 4. User review on Capterra
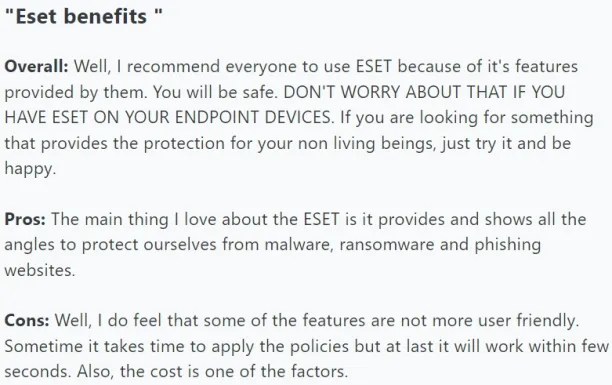
Source: Capterra.27
5. WeBroot Business Endpoint Protection
Webroot was founded in 2007. It produces security solutions for endpoints and e-mails, as well as DNS protection.
Pros
- Management console: Multiple users like the management console.28 29 30
Cons
- Malware protection: Multiple reviewers claim malware prevention has failed to work at times.31 32 33
Figure 5. WeBroot Business Endpoint Protection Pros & Cons
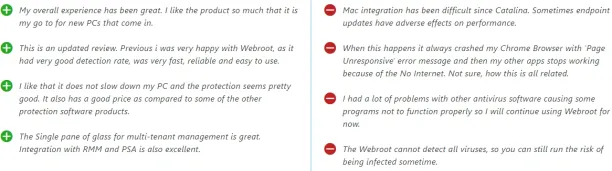
Source: Capterra.34
Further reading
- Top 9 Hexnode Alternatives Based on 10K+ Reviews
- Top 5 NinjaOne Alternatives Based on 4.5K+ Reviews
- Top 10 Endpoint Management Software: 12K+ Reviews
If you need help finding a vendor or have any questions, feel free to contact us:
External resources
- 1. “Trump signs into law U.S. government ban on Kaspersky Lab software”. Reuters. Accessed: 4/April/2024.
- 2. “Good End Point Protection but little bit slowing the machin”. G2. Accessed: 4/April/2024.
- 3. “”It has the ability to protect systems from DOS and Distributed DOS attacks!””. G2. Accessed: 4/April/2024.
- 4. “Efficient and safe”. G2. Accessed: 4/April/2024.
- 5. “Efficient Protection”. TrustRadius. Accessed: 4/April/2024.
- 6. “Simple, safe, protective”. G2. Accessed: 4/April/2024.
- 7. “Managing Kaspersky Endpoint Security for Business”. G2. Accessed: 4/April/2024.
- 8. “Kaspersky Endpoint Security Cloud is a must have security solution for stress free work life”. TrustRadius. Accessed: 4/April/2024.
- 9. “Solid Contender For A Comprehensive Endpoint Security Suite Across Multiple OS’s.”. Gartner. Accessed: 5/April/2024.
- 10. “Security across all devices using the best technology”. Capterra. Accessed: 5/April/2024.
- 11. “Trellix Endpoint Security”. Gartner. Accessed: 5/April/2024.
- 12. “I am sure about my endpoints security.”. Capterra. Accessed: 5/April/2024.
- 13. “Symantec Endpoint Security “. Gartner. Accessed: 5/April/2024.
- 14. “Symantec Endpoint Protection”. Gartner. Accessed: 5/April/2024.
- 15. “Symantec Endpoint Security Complete”. Gartner. Accessed: 5/April/2024.
- 16. “Symantec Endpoint Protection”. Gartner. Accessed: 5/April/2024.
- 17. “Symantec Endpoint Security Complete vs Trelliz Endpoint Security (ENS)”. Gartner. Accessed: 5/April/2024.
- 18. “CrowdStrike Falcon”. Capterra. Accessed: 5/April/2024.
- 19. “Essential-Falcon End Protection”. G2. Accessed: 5/April/2024.
- 20. “Efficient Endpoint Protector”. G2. Accessed: 5/April/2024.
- 21. “Best EDR currently.”. Capterra. Accessed: 5/April/2024.
- 22. “CrowdStrike Falcon Endpoint Protection Platform Features”. G2. Accessed: 5/April/2024.
- 23. “Secure by Design”. Capterra. Accessed: 4/April/2024.
- 24. “Powerful tool for Cybersecurity on Enpoints”. Capterra. Accessed: 4/April/2024.
- 25. “ESET PROTECT – ABOVE AND BEYOND”. G2. Accessed: 4/April/2024.
- 26. “ESet Endpoint Protection”. G2. Accessed: 4/April/2024.
- 27. “Eset benefits “. TrustRadius. Accessed: 4/April/2024.
- 28. “How The Mighty Have Fallen”. Gartner. Accessed: 5/April/2024.
- 29. “Webroot AV”. Gartner. Accessed: 5/April/2024.
- 30. “Great lightweight security solution”. G2. Accessed: 5/April/2024.
- 31. “Easy to manage”. G2. Accessed: 5/April/2024.
- 32. “Good Endpoint Protection But Not Good Enough “. Capterra. Accessed: 5/April/2024.
- 33. “Webroot AV”. Gartner. Accessed: 5/April/2024.
- 34. “Pros&Cons”. Capterra. Accessed: 5/April/2024.

Cem is the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per Similarweb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Sources:
AIMultiple.com Traffic Analytics, Ranking & Audience, Similarweb.
Why Microsoft, IBM, and Google Are Ramping up Efforts on AI Ethics, Business Insider.
Microsoft invests $1 billion in OpenAI to pursue artificial intelligence that’s smarter than we are, Washington Post.
Data management barriers to AI success, Deloitte.
Empowering AI Leadership: AI C-Suite Toolkit, World Economic Forum.
Science, Research and Innovation Performance of the EU, European Commission.
Public-sector digitization: The trillion-dollar challenge, McKinsey & Company.
Hypatos gets $11.8M for a deep learning approach to document processing, TechCrunch.
We got an exclusive look at the pitch deck AI startup Hypatos used to raise $11 million, Business Insider.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on


Comments
Your email address will not be published. All fields are required.