Top 10 Open Source RBAC Tools in 2024 Based on GitHub Stars
Network security statistics show that 6+ million data records were exposed globally due to data breaches in the first quarter of 2023. Companies need to protect their digital channels against malicious users.
Defining role-based access controls with conventional logic is an effective method for governing, unauthorized user access to vital company resources, however, manually dealing with hundreds of conditional statements. Instead, security teams may leverage centralized open source RBAC tools to streamline their access control procedures without the burden of license fees and vendor commitments.
Top 10 open source RBAC tools
Table 1: Market presence of top 10 open source RBAC tools
| Vendor | # of stars on GitHub | License | Supported languages | Integrations | Source code |
|---|---|---|---|---|---|
| Casdoor | 8,685 | Apache-2.0 | Go, HTML, Makefile, Less, Dockerfile, CSS | Apache DolphinScheduler, BookStack, Bytebase, Firebase, GitLab, OpenShift, Zentao | Casdoor |
| Zitadel | 7,170 | Apache-2.0 | Go, TypeScript, HTML, SCSS, CSS, JavaScript | Atlassian, GitLab, Auth0, AWS, Cloudflare Zero Trust, Nextcloud, Zoho Desk | Zitadel |
| Cerbos | 2,533 | Apache-2.0 | Go, Smarty, Shell, Makefile, JavaScript, TSQL | Okta, FusionAuth, Magic, WorkOS, Clerk, STYTCH, Microsoft Entra ID | Cerbos |
| Permit | 2,306 | Apache-2.0 | Python, Shell | Okta, Authentik, AWS Cognito, Clerk, WorkOS, Kinde, Auth0 | Opal |
| OpenFGA | 2,301 | Apache-2.0 | Java, TypeScript, Go, Ruby, Smarty | OPA, Envoy, Kong, Auth0, Okta, AzureAD | OpenFGA |
| Fairwinds | 1,411 | Apache-2.0 | Go, Shell, Python, HCL, HTML | OPA, Polaris, Kyverno | Rbac-manager |
| CyberArk | 1,280 | GPL-3.0 | Python, Shell, Ruby, Go, PowerShell | Ansible, Jenkins, Puppet, Spring Boot, Terraform | KubiScan |
| Casbin | 1,105 | Apache-2.0 | Casbin, jCasbin, node-Casbin, PHP-Casbin, PyCasbin, Casbin.NET | VMware Harbor, Intel RMD, VMware Dispatch, Skydive, Zenpress, Argo CD, Muxi Cloud, EngineerCMS | Casbin.NET |
Alcide | 874 | Apache-2.0 | Go, Shell, Makefile, JavaScript, C++ | Argo CD, Github Actions, Jenkins, Azure DevOps, Google Cloud Build, CircleCI, Travis CI, GitlabCI | Rbac-tool |
| PaloAlto Networks | 322 | MIT | Go, Open Policy Agent, Python, Shell, Makefile | Not specified | Rbac-police |
Disclaimer: Vendors are sorted based on GitHubStar numbers in descending order.
Top 10 RBAC tool selection criteria:
- Number of reviews: 300+ GitHub stars.
- Update release: At least one update was released in the last week.
Read more: RBAC use cases, RBAC examples.
1. Casdoor
Casdoor is an Identity Access Management (IAM) platform with a web interface that supports OAuth 2.0, Google Workspace, Active Directory, and Kerberos.
Casdoor supports several free services, including identity verification, role-based access control, user administration, and resource upload. Casdoor implements authentication through communication with vendors and users.
Figure 1: Illustration of authentication through communication

Source: Casdoor1
With Casdoor roles and permissions can be paired to define customizable permissions for built-in objects (such as apps) or other access behaviors. Administrators can create groups and virtual groups based on the company’s authority structure, and each group can define permissions individually.
2. Zitadel
Zitadel is an open-source identity infrastructure platform with RBAC integrations available. It combines multi-tenancy (e.g. B2B customer customer portal management), secure login, and self-service capabilities. It supports several protocols, including OpenID Connect, OAuth2.x, and SAML 2.
Video 1: Zitadel administrator console
Source: Zitadel2
Zitadel allows administrators to integrate the RBAC package and assign authorization roles from the ZITADEL Console, and permissions through the APIs.For example, administrators may use the term “roles” to refer to application-specific positions (e.g., admin, accountant, employee, human resources, etc.), and ZITADEL-specific manager roles, such as “ORG_OWNER” and “IAM_OWNER”.
When administrators expect to return they can send a cURL request that will return a list of custom user roles in the Zitadel domain. In the below example, the HR manager David Wallace’s credentials can be seen. Furthermore, administrators can customize the credentials of any allowed user through APIs.
Figure 2: Searching management grants in Zitadel
Source: Zitadel3
3. Cerbos
Cerbos is an authentication layer that allows users to design strong, context-aware access control rules for their application resources in simple, intuitive YAML syntax policies, which are maintained and distributed via Git-ops infrastructure. With Cerbos, users can:
- Collaborate with teammates to create and share policies in fully interactive private environments.
- Deliver network security policy updates to your entire packet data protocol (PDP) fleet.
- Create custom policy bundles for client-side or in-browser authorization.
Figure 3: How Cerbos integrates with your application

Source: Cerbos4
4. Fairwinds – RBAC Manager
RBAC Manager is created to ease Kubernetes authorization. RBAC Manager allows users to customize role bindings or service account settings instead of manually maintaining configurations.
RBAC Manager has three primary goals:
- Offering an open-ended approach to RBAC that is more accessible and flexible.
- Minimizing the amount of settings necessary for effective authentication.
- Automating execution of RBAC configuration modifications with CI/CD (continuous integration/continuous delivery).
To illustrate how RBAC Manager works, consider a basic example. In this example, we’ll have a single user, Joe, who requires “edit” access to the “web” namespace with RBAC. This involves creating role bindings that allow edit access to the web namespace.
Figure 4: Role binding with Fairwinds – RBAC Manager

Source: Fairwinds5
5. Permit – Opal
OPAL is an administrative layer for policy engines such as open policy agents (OPA) that detects policy and data changes in real-time and sends live updates to administrators, allowing them to customize role-based permissions.
When administrators navigate to the user interface, administrators can update each user’s role-based attributes. These attributes are subsequently transferred to the Permit backend and placed with the user’s information in the database.
When administrators execute permit.check() on an individual user to check his access, these attributes are dynamically imported into the function, and assessed based on the policy and the user attributes.
Video 2: User permission checks in the UI with Opal
Source:Permit.io6
6. CyberArk – KubiScan
KubiScan is a tool for screening the Kubernetes cluster for risky permissions in the role-based access control (RBAC) authorization plan.
KubiScan assists cluster administrators in identifying permissions that attackers may use to breach the cluster. This can be especially useful in large setups with several permissions that might be difficult to track. KubiScan collects information on risky roles, cluster roles, role bindings, users, and pods to simplify laborious operations and provide administrators with the necessary insight to decrease permission risks. KubiScan can:
- Detect risky roles\cluster roles.
- Detect risky role bindings\cluster role bindings.
- Detect risky subjects (e.g. users, groups, and service accounts).
- Detect risky pods\containers.
- List subjects with specific kinds (‘user’, ‘group’, or ‘service account’).
- List rules of role binding or cluster role binding.
Video 3: An example of KubiScan usage to detect risky permissions
Source: Cyberark7
7. OpenFGA
OpenFGA is an open-source fine-grained authorization system built on Google’s Zanzibar*. It is intended to enable application developers to quickly add fine-grained authorization based on user groups to their apps. It provides an HTTP API and software development kit (SDK) for programming languages such as JavaScript, GoLang, and.NET. More SDKs and interfaces, including Rego, are planned for the future. With OpenFGA administrators can:
- Write an authorization model
- Write relationship tuples
- Perform authorization checks
- Add authentication to their OpenFGA server
For example, to check if user “user:anne” of type user has a “reader” relationship with object “document:2021-budget” administrators can write tuples to check APIs. Thus. the query in figure will always return { “allowed”: true }if the user sets “document:2021-budget#reader” have the “reader” relation with “document:2021-budget”
Figure 5: Querying with contextual tuples

Source: OpenFGA[efn note]”OpenFGA API Documentation” OpenFGA. 2024. Retrieved May 10, 2024.[/efn_note]
*Zanzibar is part of “Google’s global authorization system” aimed at “determining whether online users have permission to access digital objects”.
8. Casbin – Casbin.Net
Casbin is an open-source access control library that can be used to enforce permission.
Casbin’s model file gives the administrator full control over the authorization conditions, allowing administrators to enforce rules, and list subjects/objects.
Casbin is an authorization library that may be used in situations where companies expect to see a specified user or subject to have access to a given object or entity. With Casbin administrators can set a type of access, or action, to be “read”, “write”, “delete”, or any other action. Casbin abstracts an access control model into a “CONF” file using the (policy, effect, request, and matches) “PERM” model, allowing users to change or update a project’s authentication method.
Figure 6: The PERM model code
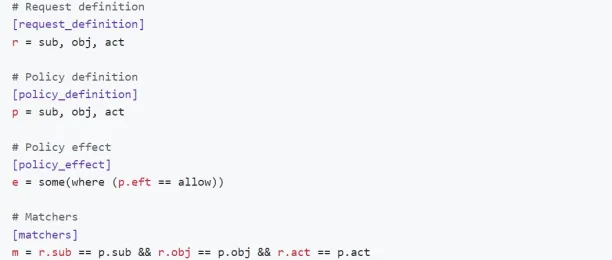
Source: Casbin8
In addition to the typical flow, Casbin can handle several intricate permission circumstances. Roles (RBAC), attributes (ABAC), and others. Casbin can:
- Implement the policy using a customized form as specified or the traditional {subject, object, action} form. Authorizations can be granted or denied.
- Govern the policy and model storage for access control.
- Oversee the role-user and role-role mappings, also known as the role hierarchy in RBAC.
- Offer a variety of integrated operators to facilitate rule matching. KeyMatch, for instance, can match the “pattern /foo*” to the resource “key /foo/bar”.
The most fundamental and simple model in Casbin is the access control list (ACL). The ACL model “CONF” is:
Figure 7: Role-based access control list (ACL)

Source: Casbin9
Which means:
- alice can read data1
- bob can write data2
9. Alcide
Alcide is an RBAC tool for Kubernetes that enables DevOps teams to build security barriers into their CI/CD pipelines and security teams to defend their Kubernetes deployments. Alcide offers a single Kubernetes-native AI-driven security platform for all Kubernetes-related features, including configuration risks, cluster visibility, and run-time security events.
Alcide’s RBAC authorization leverages the “rbac.authorization.k8s.io” API group to make authorization choices, allowing users to set rules via the Kubernetes API dynamically.
Users can use Role or ClusterRole to:
- Define rights on namespaced* resources and grant them inside a particular namespace(s).
- Define permissions on namespaced objects and grant them across all namespaces.
- Define permissions for cluster-scoped resources.
*A namespace is a collection of signs (names) for identifying and referring to various object types.
Table 2: Roles and cluster roles used attached to user or groups
| Subject | Subcect type | Scope | Namespace | Role | Binding |
|---|---|---|---|---|---|
| system:anonymous | User | Role | kube-public | kubeadm:bootstrap-signer-clusterinfo | kubeadm:bootstrap-signer-clusterinfo |
| system:authenticated | Group | Cluster role | system:basic-user | system:basic-user | |
| system:authenticated | Group | Cluster role | system:public-info-viewer | system:public-info-viewer | |
| system:authenticated | Group | Cluster role | system:discovery | system:discovery | |
| system:bootstrappers | Group | Cluster role | system:certificates.k8s.io:certificatesigningrequests:nodeclient | kubeadm:node-autoapprove-bootstrap | |
| system:bootstrappers | Group | Role | kube-system | kube-proxy | kube-proxy |
| system:kube-controller-manager | User | Cluster role | system:kube-controller-manager | system:kube-controller-manager |
10. Palo Alto Networks – Police Tool
Palo Alto Network’s RBAC Police Tool can get the RBAC permissions of Kubernetes identities, including service accounts, pods, nodes, users, and groups by using policies created in Rego language. The policy library contains 20+ rules that detect identities with dangerous permissions, based on a distinct attack pattern. With Police tools users can:
- Inspect the permissions of specific identities
- Configure violation types
- Create custom policies
- Scope a namespace
Figure 8: A custom policy example with the Police Tool

Source: Palo Alto Networks10
With the Palo Alto Network Police Tool, administrators can define specific RBAC policies. In the example:
- The “describe” rule specifies the description and severity of the policy.
- The “targets” set specifies whose identities the policy assesses and generates violations for.
- The “evaluateRoles” function gets the roles of a serviceAccounts, node, user, or group and assesses if they violate policy.
Read more: RBAC use cases, RBAC examples.
Benefits of open source RBAC tools
Open source RBAC tools allow users to:
- Interact with fellow developers to report and track bugs and feature requests with transparency.
- Follow the latest development version and view how development is proceeding.
- Fix bugs and implement features if you know how to code.
- Avoid initial price payments, subscription fees, and vendor lock-in.
What to look out for when choosing an open source RBAC tools
Here are a few recommendations to consider while selecting an open source RBAC tool:
- Check the tool’s popularity: The number of GitHub contributors and community members responding to user inquiries reflects the popularity rate of open source technologies. The larger the community, the more support your organization can get.
- Check the tool’s features: Most open source RBAC tools provide role customization, permissions registration, and login methods. However, if your organization expects to use the RBAC tool for diverse purposes you should look for a more complete product. For example, an organization looking for automated access management might consider a solution with identity access management (IAM) features.
- Compare closed-source solutions: Open source solutions usually include limited or add-on features, implementing a more tailored solution that offers a higher level of features (e.g. cloud segmentation) can be more efficient for your organization. Here is a list of closed-source microsegmentation tools with RBAC features.
For guidance on choosing the right tool or service, check out our data-driven sources: network security policy management (NSPM) tools and incident response tools.
Further reading
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
- Top 10 SDP Software Based on 4,000+ Reviews
- Top 10 Network Security Audit Tools Based on 4,000 Reviews
AIMultiple can assist your organization in finding the right vendor.
External Links
- 1. ”Casdoor”. Casdoor. 2024. Retrieved May 9, 2024.
- 2. “Zitadel” GitHub. 2024. Retrieved May 10, 2024.
- 3. ”Retrieve User Roles in ZITADEL”. Zitadel. 2024. Retrieved May 9, 2024.
- 4. ”Cerbos”. GitHub. 2024. Retrieved May 9, 2024.
- 5. ”Fairwinds”. GitHub. 2024. Retrieved May 9, 2024.
- 6. ”Permit.io/Docs”. Permit.io 2024. Retrieved May 10, 2024.
- 7. ”Cyberark”. Cyberark. 2024. Retrieved May 9, 2024.
- 8. ”Casbin”. GitHub. 2024. Retrieved May 9, 2024.
- 9. ”Casbin”. GitHub. 2024. Retrieved May 9, 2024.
- 10. ”Palo Alto Networks”. GitHub. 2024. Retrieved May 9, 2024.

Cem is the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per Similarweb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Sources:
AIMultiple.com Traffic Analytics, Ranking & Audience, Similarweb.
Why Microsoft, IBM, and Google Are Ramping up Efforts on AI Ethics, Business Insider.
Microsoft invests $1 billion in OpenAI to pursue artificial intelligence that’s smarter than we are, Washington Post.
Data management barriers to AI success, Deloitte.
Empowering AI Leadership: AI C-Suite Toolkit, World Economic Forum.
Science, Research and Innovation Performance of the EU, European Commission.
Public-sector digitization: The trillion-dollar challenge, McKinsey & Company.
Hypatos gets $11.8M for a deep learning approach to document processing, TechCrunch.
We got an exclusive look at the pitch deck AI startup Hypatos used to raise $11 million, Business Insider.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on

Comments
Your email address will not be published. All fields are required.