Role-based access control (RBAC) in 2024
This article covers a complete explanation of role-based access control (RBAC) along with a step-by-step guide explaining how RBAC works, and how organizations can orchestrate it to meet their network security policies against the most common cyber attack vectors.
What is Role-based access control (RBAC)?
Role-based access control (RBAC) is a way of controlling network accessibility depending on the authority of each user within an organization.
Organizations can implement RBAC with microsegmentation tools, also known as role-based security, to segment network access levels depending on an employee’s position and responsibilities and classify them into “roles based” on related duties.
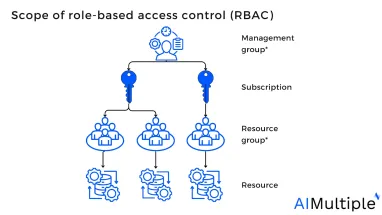
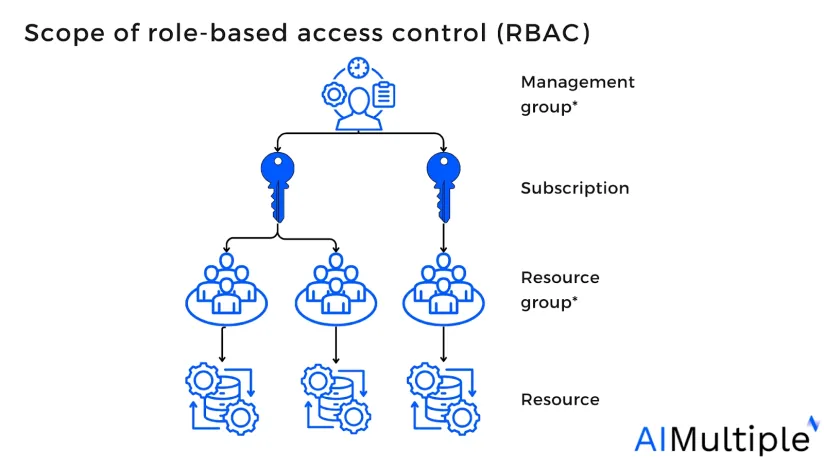
Figure: Role relationship
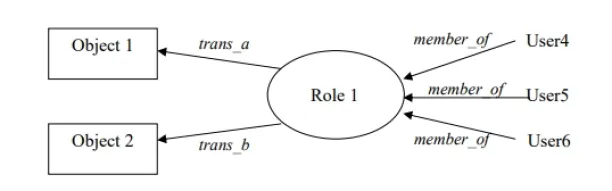
Source: Ferraiolo, D.F.; Kuhn, D.R.1
Why is role-based access control (RBAC) important?
Limiting network access is critical for companies with several employees, contractors, or third-parties – such as vendors or consultants – as constantly supervising network access can be challenging. Companies that rely on RBAC are more capable of network access control (NAC) and managing essential applications/services.
RBAC can help companies limit network access depending on variables such as authority, expertise, and responsibility, prohibiting them from gathering nonrelevant information.
For example, organizations can use RBAC to:
- Limit their network access, such as entry to certain files or applications.
- Regulate admission to an application or service to provide certain employees the ability to access and edit records.
4 Types of role-based access control
1. Core: The core model defines the key components of any role-based access control system. While core RBAC may be used as a stand-alone access control approach, it also serves as the foundation for both hierarchical and constrained approaches.
It can be used on its own or as the foundation for hierarchical and constrained RBAC. Users, roles, permissions, operations, and objects are the five static components of core RBAC.
Core RBAC follows three rules:
1. A user can only work at a job if they have been allocated a role entailed with that job function.
2. An administration has to assign a certain role(s) to a particular user.
3. A user can only have access to a certain job if their role is related to that job.
2. Hierarchical: Hierarchical role-based access control establishes linkages between roles (e.g., senior, mid-level, junior) by using a hierarchy inside the role framework. Authorized users with senior positions in hierarchical RBAC can allow all of their juniors’ permissions along with their requirements.
3. Constrained: Constrained RBAC enhances the core model’s assignment of roles by enabling administrators to separate roles that are classified as static and dynamic.
- Static: A single user under Static Separation of Duty (SSD) cannot hold mutually exclusive roles. This eliminates discretionary access control, for example, one person cannot concurrently request and approve an expenditure.
- Dynamic: A user under the Dynamic Separation of Duty (DSD) model can have opposite roles. However, the user may not perform both tasks in the same session.
4. Symmetric: Administrators can undertake both permission-role and user-role assessments using symmetric RBAC control.
RBAC permissions
When assigning user permissions, organizations can determine the type of permission assigned for each user by customizing what each position should accomplish when using role-based access control.
Access
- Which users have access to a certain object, such as a file, program, or database?
- Which users need to be notified of the accessibility of specific resources?
- What restrictions should be imposed on visibility?
Customization
- Which users can make adjustments to particular items?
- What authorizations are necessary to make adjustments?
Sharing
- Who may download a file?
- Which users can share a file?
A set of permissions that allows users to read, edit, or delete articles in an article-writing software is an example of role-based access control. The following table shows the authorization levels for three roles: senior writer, writer, and reader.
Table: Role-based access control table designed for article-writing software
| Role | Senior writer | Writer | Reader | |
|---|---|---|---|---|
| Edit | ✅ | ✅ | ✖ | |
| Delete | ✅ | ✖ | ✖ | |
| Read | ✅ | ✅ | ✅ | |
Below are the key components of the role-based approach to access control:
User: An individual who has access to a network and has a unique identity (UID).
Role: A role is a specific work activity that determines the amount of authority (e.g. administrator, manager, user).
Session: An interval of work time when a user makes use of the rights granted to them by their responsibilities.
Object: An internal asset that must be accessed with authorization.
Operation: Any action in the secured network is referred to as an operation.
How does role-based access control (RBAC) work?
RBAC works by limiting resource access by assigning roles.
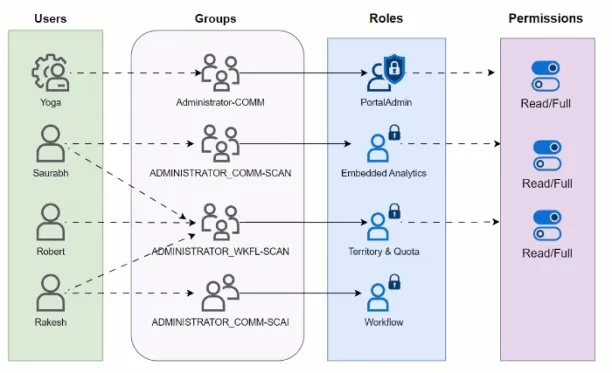
A role assignment is a method of associating a role description with a user, group, service principal, or managed identity at a certain scope to grant access.
The figure below illustrates an example of a role assignment. The IT group has been allocated the Contributor role for the sales resource group. Users in the IT group can thus create or administer any resource in the sales resource group (IT users do not have permission to use resources other external resources than the sales group’s resources.). Unless they are assigned to another “role.
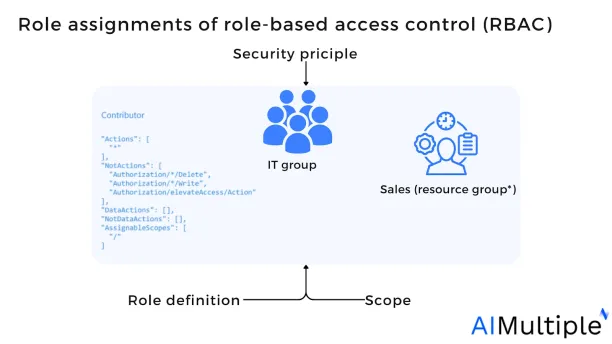
*Group: Role assignments are bidirectional for groups, hence if a user is a part of one group and that group is a member of another group that is assigned a role assignment (e.g. editor), the user will have access to specified (e.g. editor access).
3 Parts of role assignment
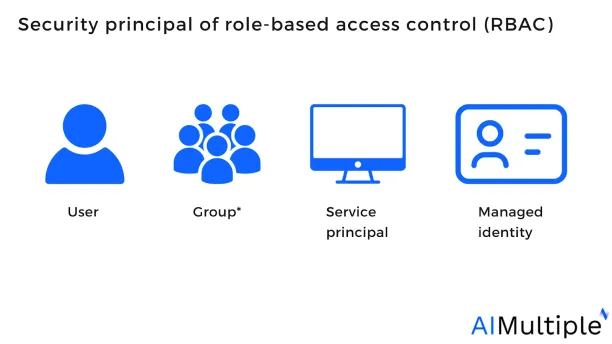
1. Security principal
A security principle is an object representing a user, group, service principal, or managed identity seeking user access to resources over a network. Administrators can allocate a role to any security principle.
2. Role definition
A role definition is a set of permissions given for a particular activity (e.g. reading, writing, or deleting activities) that are listed in a job definition. Roles might be wide-ranging, such as “Administrator”, or limited, such as “TestPermission”. Administrators can define a role to be assigned to one or more cybersecurity principals.
Figure: Example of a role definition ID of “1073741928” with custom permission level “TestPermission”

Source: Code Project2
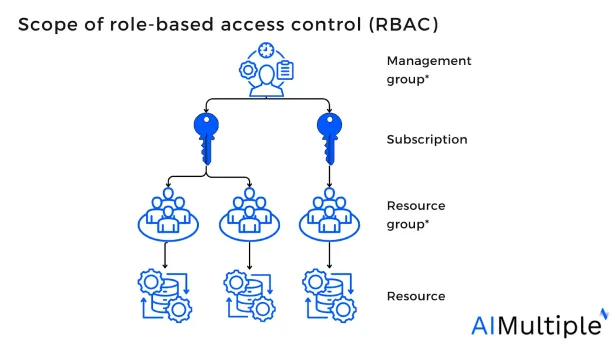
3. Scope
The scope is the collection of resources within the access management process. When administrators label a role, users may further restrict (restricting network access based on constraints) the actions that are allowed by establishing a scope. This is useful if organizations expect to add a user as a “contributor” for a single group.
Scopes are organized in the form of a top-down relationship. Organizations may delegate responsibilities at any of these scope levels.
Final overview of RBAC: After the role assignment is set up, suppose a user attempts to access an application, the RBAC system will initially check the roles connected with the user and then see whether any roles have the necessary permissions. If this is the case, the user can use the application. Otherwise, the user is refused access.
Figure: High-level flow of RBAC
Source: SAP3
RBAC implementation
Demonstration of RBAC bash script in ASP.NET Core
Illustration of an RBAC implementation in an ASP.NET Core MVC web application. It primarily entails using the Authorize attribute-based access control to specify which roles should be permitted to have access to particular devices.
An application registration script with app roles and assignments for defining roles is shown below.
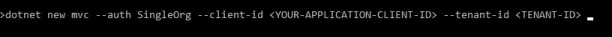
- The code uses the .NET command-line interface (CLI) to develop a new ASP.NET Core MVC web application.
- Then, the code specifies the –auth flag with either “SingleOrg” or “MultiOrg” for single user login, the “–client-id” notice with the client if from application login, and the “–tenant-id” notice with the user if from non-application login.
Adding role-based authorization in ASP.NET
When an identity is formed, it may be assigned to several roles. Bert, for example, may have both the Administrator and User roles, whereas Emma might only have the User role. The sensitive data stored in the permission procedure determines how these classifications are assigned.
Multiple roles (HRManager, Finance) can be assigned in a comma-separated list: Users with the –HRManager or –Finance roles have access to the –SalaryController “controller” role.
Figure: Adding roles to employees in ASP.NET Core by writing code on C#

Source: Microsoft4
Limits can be assessed to users by formulating additional attributes at the action level. Thus, the accessing user can be granted for both the –PowerUser and –ControlPanelUser roles:
Figure: Adding action-level roles to employees in ASP.NET Core by writing code on C#
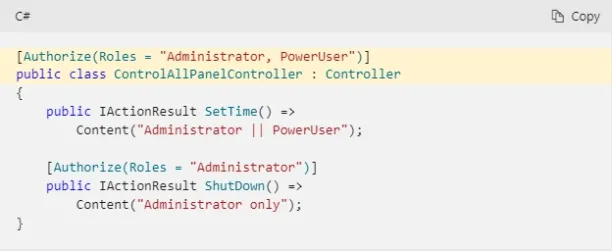
Source: Microsoft5
Benefits of RBAC
Enhanced operational efficiency: Companies can use RBAC to reduce the need for documentation and password changes when hiring freshers or changing the responsibilities of current employees. Companies may quickly establish and modify roles, and then apply them among platforms, operating systems, and apps, using RBAC.
Decreased risk of data breaches: Employing RBAC involves formulating security risk assessment and limiting access to private data, and lowering the risk of data breaches or leaking.
Improved data protection: RBAC follows the rule of least privilege (PoLP), a fundamental concept of zero-trust architecture, which states that a user is only provided the user privileges necessary to do their job. By regulating access in this way, companies may eliminate unwanted dangers and the possibility of data breaches—along with the associated expenses.
More control over regulatory compliance: Using pre-determined role structures improves visibility, supervision, and auditing. Administrators can discover and remedy errors in user permissions, enabling improved regulatory data compliance (HIPAA, GDPR, SOX, SOC 2, and ISO 27001) and more accurate control over access to critical systems and data.
Streamlines workflows: RBAC offers users the precise access required for their responsibilities, eliminating bottlenecks. With RBAC Employees will no longer be required to press administrators for access to information and systems, and IT can become free of the burden of managing one-time authorization for each user.
For example, RBAC can provision tasks such as onboarding and offboarding. Administrators may simply leverage fine grained access control such as granular access controls by customizing permissions for current employees who change responsibilities within the business, plus consultants, vendors, or third-party users who require temporary network access.
Increased network visibility: RBAC provides a scope of network activities (an overview of who has access to what they need to execute their tasks) so that administrators and managers will have improved insights and visibility into the organization.
For guidance on choosing the right tool or service for your project, check out our data-driven lists of software-defined perimeter (SDP) software and zero trust networking software.
Further reading
- Top 10 Microsegmentation Tools in 2024
- Top 10 Insider Threat Management Software
- Microsegmentation in 2024: What is it? Benefits & Challenges
- Zero Trust Network Access (ZTNA) in 2023: Definition & Benefits
- 10 Cybersecurity Best Practices for Corporations
External links
External Links
- 1. “Role-Based Access Control” (PDF). October 1992. Retrieved December 27, 2023.
- 2. “Get SharePoint Role Definition IDs“. Code Project. October 11, 2020. Retrieved December 27, 2023.
- 3. “SAP Commissions – Implementing Authorization With User Roles (RBAC)“. SAP. November 21, 2022. Retrieved December 27, 2023.
- 4. “Role-based authorization in ASP.NET Core“. Microsoft. July 14, 2023. Retrieved December 27, 2023.
- 5. “Role-based authorization in ASP.NET Core“. Microsoft. July 14, 2023. Retrieved December 27, 2023.

Cem has been the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per similarWeb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised businesses on their enterprise software, automation, cloud, AI / ML and other technology related decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on

Comments
Your email address will not be published. All fields are required.