Top 10+ Software Composition Analysis (SCA) Tools for 2024
Software composition analysis (SCA) has become crucial with the growing adoption of open source in software development.1 Software composition analysis allows development teams to efficiently monitor and assess any open-source component. However, not all SCA solutions offer the same features and advantages. SCA tools may vary in their capabilities and effectiveness.
This article explores the leading software composition analysis solutions, providing insights into their key features and pricing structures.
Top software composition analysis tools
| Competitor | SBOM generation* | On-premises deployment ** | Starting price/mo | Free trial |
|---|---|---|---|---|
| Invicti Shark | ✅ | ✅ | Custom | ✅ |
| Aikido Security | ✅ | ✅ | $349 | Free plan |
| Checkmarx | ✅ | ✅ | Custom | ✅ |
| JFrog X-Ray | ✅ | ✅ | $150 | ✅ |
| Mend.io | ✅ | ✅ | $1,500 | N/A |
| Qwiet AI | N/A | ✅ | N/A | ✅ |
| SOOS | ✅ | ❌ | $100 | ✅ |
| Spectral | ✅ | ✅ | N/A | N/A |
| Snyk Open Source | ✅ | ❌ | Custom | Free plan |
| Synopsys Black Duck | ✅ | ✅ | $525 | ✅ |
| Veracode | ✅ | ❌ | Custom | ✅ |
Vendors are listed in alphabetical order, except for the products of the sponsors of the article, which include links to the sponsors’ websites.
Table notes:
- SBOM generation*: SBOM, which stands for “Software Bill of Materials,” includes detailed information about the versions of components, their sources, and their interdependencies.
- On-premises deployment **: Refers to the installation and operation of software directly on the physical hardware located within an organization’s own servers or computer systems.
1. Invicti Shark (IAST & SCA)
Invicti Shark is an interactive application security testing (IAST) tool that can gather details on installed software package managers and pinpoint all third-party components used in a web application. It is capable of conducting software composition analysis (SCA) by identifying these components within a web application and listing them under the software composition analysis section in the knowledge base.
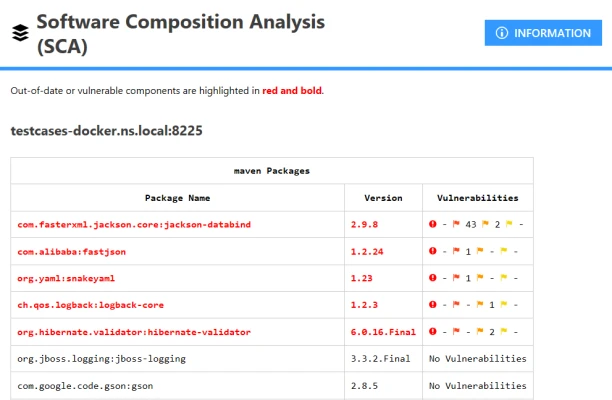
2. Checkmarx SCA

Checkmarx is a software security company that provides solutions to integrate security across all phases of the software development lifecycle (SDLC). Its application security testing (AST) platform features a range of tools including static application security testing (SAST), software composition analysis (SCA), API security, and dynamic application security testing (DAST).
Checkmarx SCA specifically focuses on monitoring open-source components used in applications and offers guidance for remediation. This solution is tailored for secure DevOps environments. Additionally, Checkmarx SCA allows for the definition of specific open-source security policies for individual projects.
3. Synopsys Black Duck Software Composition Analysis
Synopsys Black Duck is a software composition analysis (SCA) tool that examines codebases to detect open-source components, identify known vulnerabilities, and assess license compliance in applications and containers.
The Black Duck professional edition offers both on-premises and hosted solutions that scan source code for open-source vulnerabilities and licensing risks. Additionally, Black Duck includes a binary analysis add-on designed to evaluate third-party-compiled code. This makes it especially appropriate for enterprises in tightly regulated sectors, where managing licenses and intellectual property, along with detecting vulnerabilities, is crucial.
4. Snyk Open Source

Snyk offers a developer-focused SCA solution that identifies and addresses and fix security vulnerabilities in open-source dependencies. Synk’s software composition analysis tool reviews pull requests (PRs) prior to merging. The solution allows security teams to conduct testing of their projects directly within the repository and keep a daily check for any emerging security vulnerabilities.
Snyk’s pricing is per developer, per month, and includes unlimited tests for open-source components, container scanning, and infrastructure as code (IaC).
5. Veracode Software Composition Analysis

Veracode’s SCA tool detects vulnerabilities within open-source libraries and the other software components they rely on. Veracode’s scans a list of libraries within an application and proceeds to identify the documented vulnerabilities within each library. Additionally, the SCA tool alerts users to recently disclosed vulnerabilities affecting applications, eliminating the need for a new application scan.
Veracode SCA offers two scanning approaches that can be executed at various stages of the development process:
- Upload and scan method: Scans application subsequent to compiling and uploading its binary files onto the Veracode Platform.
- Agent-based scan method: Conducts code scans at the outset and at regular intervals throughout software development lifecycle (SDLC).
6. Aikido Security

Aikido SCA maintains continuous monitoring of code to detect known and common vulnerabilities, CVEs, and other potential security risks. When Aikido identifies a known vulnerability, it employs a reachability analysis engine to verify if software applications can indeed access this vulnerable code. This approach aids in minimizing false positives and irrelevant notifications.
Aikido’s reachability engine disregards a CVE if the codebase doesn’t invoke the vulnerable function, reducing unnecessary alerts, particularly for extensive libraries with numerous direct and indirect dependencies. The solution provides a single CVE alert for each repository, accompanied by sub-issues detailing the location of each security vulnerability.
7. JFrog X-Ray SCA

JFrog Xray’s SCA integrates with Artifactory, helping developers to identify vulnerabilities, uphold open-source licensing regulations, and encourage the reuse of artifacts across the software development lifecycle. Xray Cloud operates on Amazon Web Services, Google Cloud Platform, or Microsoft Azure infrastructure. It incorporates JFrog’s vulnerabilities database, which includes data from various sources such as NVD, GitHub, Ubuntu, Debian, Red Hat, PHP, along with insights from the JFrog Security Research team, providing precise details on detected vulnerabilities.
8. Spectral

The Spectral SCA solution is ideal for DevOps teams engaged in medium to large-scale projects, providing rule development capabilities and versatile customization features. The tool examines dependencies to safeguard the software supply chain and pipeline against license compliance issues and vulnerabilities originating from open-source software, incorporating source code analysis tailored specifically for developers.
9. SOOS SCA
SOOS offers a cloud-based software composition analysis tool designed to scan and identify vulnerable packages, providing guidance on how to address them. It seamlessly integrates into the development team’s CI/CD pipeline and other workflow tools. During an SCA scan of your package manifests, SOOS cross-references your packages with those listed in relevant databases. Any matches found are promptly reported as vulnerabilities.
10. Qwiet AI

Qwiet AI Software Composition Analysis (SCA) employs a Code Property Graph (CPG) alongside its proprietary AI/ML engine to scrutinize the data flow throughout an entire application. Qwiet can assess the container housing your application to uncover findings that may not be directly linked to your application.
The platform supports both Linux- and Windows-based containers; however, analyzing Windows-based containers is currently limited to Windows machines. With Qwiet SCA, users can filter security issues based on severity level, status, and assignee for subsequent actions. Qwiet provides various methods for obtaining licensing information for open-source packages, including SBOM and API. The SBOM report, automatically generated for each submitted application, includes a column indicating the license for each dependency. The API delivers findings for an application, along with associated tags for each finding.
11. Mend SCA

Mend Software Composition Analysis platform assists organizations in overseeing their open-source components. It conducts security scans to identify vulnerable dependencies and offers insights into licensing issues. Mend SCA facilitates the compilation of a Software Bill of Materials (SBOM) for dependencies, providing users with a comprehensive view of all open-source libraries and dependencies utilized.
The solution integrates with IDEs, repositories, registries, and CI/CD pipelines. Additionally, Mend enables organizations to identify vulnerabilities in container image layers before they are deployed to production environments.
What is software composition analysis (SCA)?
Software Composition Analysis (SCA) is a method employed in application security to manage the third-party and open-source elements integrated into a software application. These elements include libraries, frameworks, and additional software modules.
If you have further questions, reach us.
External Links
- 1. Vailshery, L. (Oct 25, 2023) “Total number of global open source projects adopted 2023“. Statista


![Data Quality Tools & Criteria for Right Tools [2024 update]](https://research.aimultiple.com/wp-content/uploads/2018/06/data-cleaning-tools-190x110.png.webp)
Comments
Your email address will not be published. All fields are required.