Enterprise Network Monitoring in 2024: 7 Best Practices
Enterprise network monitoring is not a singular activity but a complex of various monitoring facets, each playing a significant role in the overall health of the network. This guide delves into enterprise network monitoring, its components, and best practices to optimize its use for the benefit of businesses.
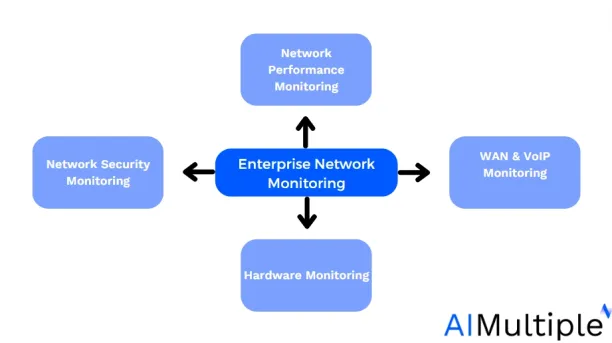
- Network performance monitoring: At the heart of enterprise monitoring is network performance monitoring. Monitoring tools here are designed to detect and report issues like bandwidth bottlenecks, latency problems, and packet loss.
- Hardware monitoring: Network infrastructure is only as strong as its weakest link, which often comes down to the physical hardware. Hardware monitoring focuses on the health and status of all physical devices within the network.
- WAN & VoIP monitoring: With businesses increasingly relying on wide area networks (WAN) and Voice over Internet Protocol (VoIP) services, monitoring these aspects has become essential. WAN monitoring looks at the performance and reliability of external network connections, while VoIP monitoring ensures that voice communications are clear, reliable, and uninterrupted.
- Network security monitoring: This involves scrutinizing network traffic and activities to detect and mitigate potential security threats. From unauthorized access attempts to suspicious data transfers, security monitoring tools play a critical role in protecting sensitive network data and maintaining the integrity of enterprise networks.
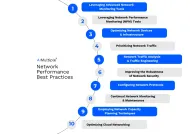
What are the best practices for enterprise network monitoring?
- Set Clear Goals: Establish objectives for enterprise network monitoring, including performance optimization, security threat detection, regulatory compliance, and capacity planning to guide your strategy effectively and align with business objectives.
- Choose the Right Monitoring Tools: Select scalable solutions like AKIPS, PRTG, Nagios, and ManageEngine to ensure adaptability to evolving enterprise network architectures, covering diverse aspects from device performance to application health.
- Implement Layered Monitoring: Employ a multi-layered approach covering device performance, application health, and network traffic analysis for comprehensive visibility into enterprise networks, enabling efficient detection and resolution of issues.
- Establish Baseline Metrics: Define key performance indicators (KPIs) such as bandwidth usage, latency, packet loss, and error rates, and establish baseline metrics to understand normal behavior, facilitating effective performance monitoring and troubleshooting.
- Set Up Alerts and Notifications: Configure proactive alerts based on threshold values for timely responses to critical issues in enterprise networks, ensuring automated notifications via email, SMS, or other channels to facilitate prompt action.
- Empower for Competence: Automate routine tasks such as configuration management and incident response in enterprise network monitoring, regularly testing automation scripts to ensure reliability and efficiency in managing network operations.
- Conduct Periodic Audits and Reviews: Perform regular performance audits and security assessments in enterprise network monitoring to identify improvement areas and maintain compliance with security policies, ensuring the network operates optimally and securely.
- Ensure Full Reveal: Monitor all network segments, including remote sites, cloud services, and IoT devices, ensuring comprehensive visibility across the entire enterprise network infrastructure to detect and address issues effectively.
- Infuse Monitoring into Security Infrastructure: Integrate network monitoring with Security Information and Event Management (SIEM) systems in enterprise networks for comprehensive security monitoring and real-time threat detection, enhancing overall network security posture.
- Encourage Documentation and Collaboration: Foster collaboration between teams involved in enterprise network monitoring, maintaining up-to-date documentation of network topology, configurations, and processes to ensure consistency, compliance, and efficient incident response.
If you are looking for free network monitoring tools that align with the best practices discussed in this article, consider exploring our guide ‘Top 7 Free Network Monitoring Tools.‘ This resource offers a selection of effective solutions that can help you enhance your network management without incurring additional costs.
FAQ
What is enterprise network monitoring?
Enterprise network monitoring is an integral process that involves the continuous observation and management of an organization’s network infrastructure. It’s a systematic approach to oversee all network devices, ensuring they function optimally and securely. This monitoring encompasses a wide range of activities, from analyzing network traffic flows to maintaining network security, and plays a vital role in the stability and efficiency of enterprise networks.
For more on network monitoring
If you have questions or need help in finding vendors, reach out:

Cem is the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per Similarweb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Sources:
AIMultiple.com Traffic Analytics, Ranking & Audience, Similarweb.
Why Microsoft, IBM, and Google Are Ramping up Efforts on AI Ethics, Business Insider.
Microsoft invests $1 billion in OpenAI to pursue artificial intelligence that’s smarter than we are, Washington Post.
Data management barriers to AI success, Deloitte.
Empowering AI Leadership: AI C-Suite Toolkit, World Economic Forum.
Science, Research and Innovation Performance of the EU, European Commission.
Public-sector digitization: The trillion-dollar challenge, McKinsey & Company.
Hypatos gets $11.8M for a deep learning approach to document processing, TechCrunch.
We got an exclusive look at the pitch deck AI startup Hypatos used to raise $11 million, Business Insider.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on
Comments
Your email address will not be published. All fields are required.