11 Real-life Microsegmentation Use Cases in 2024
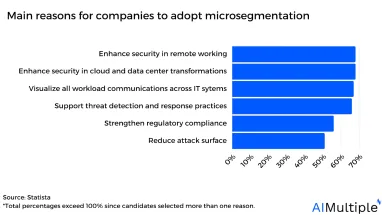
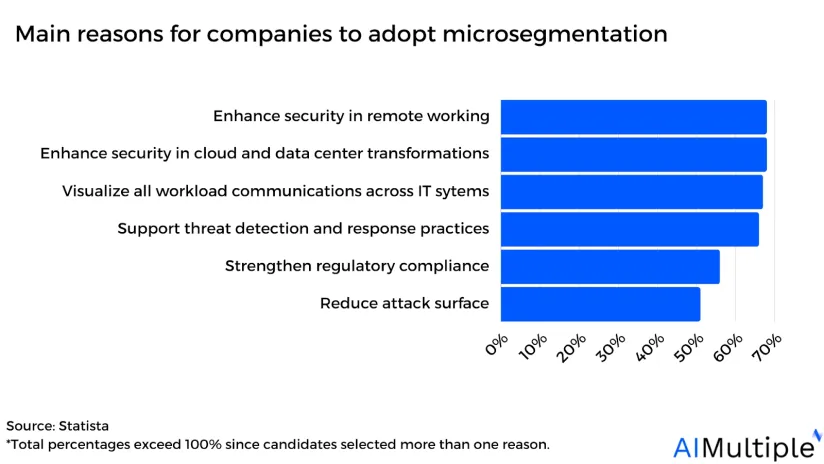
Source: Statista1
Microsegmentation is a technique for logically creating smaller network segments and controlling traffic between them. Organizations can use microsegmentation tools powered with role-based access control (RBAC) features for enhanced network visibility, intrusion prevention, and OT network segmentation against the most common cyber threat vectors.
This article discusses the 11 real-life microsegmentation use cases, examining how network teams create sub-networks with unique security controls and services in various business processes.
11 Real-world use cases of microsegmentation
1. Cloud segmentation
Cloud segmentation divides a cloud environment into separate parts, and improves security by limiting communication between them. During the cloud segmentation process, a microsegmentation policy can be set up to allow traffic between selected cloud servers such as data cloud (DevVPC) or an external system (e.g. AWS region) while blocking all other internet traffic.
Example: In cloud environments, security groups and tagging (e.g. team1-dev, DevVPC) can be added for uniform security policy modifications across resources with comparable features. Then, administrators can deploy cloud-ready firewalls (firewalls with advanced security capabilities such as IPS tools, deep packet inspection (DPI), and application-aware filtering) as virtual appliances to allow fine-grained zones (e.g. DecVPC, AWSRegion) over traffic flow across cloud segments.
Figure 1: Internal cloud segmentation for developers

Source: Tecracer2
2- API segmentation
Microsegmentation can assist API security by separating network segments for API traffic. Each segment may then be assigned unique security policies that restrict access to API endpoints, maintaining that only approved traffic is permitted. This method can help companies secure their APIs and decrease the chance of security breaches.
With API segmentation, organizations can:
- List their workspace sources and destinations to understand how data travels across their network segment.
- Set up additional configurations to deliver data to their analytics service or data storage (e.g., limiting requests per second).
- Accept and remove destinations to route data (e.g. allowing or restricting traffic to specific IP addresses).
- Prevent traffic that fits specific patterns or contents.
Example: Users can add a segment group via API in microsegmentation tools by importing packages such as pyZscaler. Users can create a “Sales Apss” or “Accounting Apps” for that group as shown below:

Additionally, users can configure the API segmentation by allowing only selected IP addresses to access “Sales Apps” or “Accounting Apps”. For example, after creating application groups that only contain sales apps, the administrators can assign the sales employee’s IP address to that group, hence only salespeople will have access to it.

3. ICS/OT segmentation
Microsegmentation allows industrial control system (ICS) owners to design a zero-trust arhitecture which allows each firewall to assign a unique IP address range to each process group. This means that a programmable logic controller (PLC) cannot connect with another PLC unless expressly approved by the network security policy, even if both PLCs are on the same VLAN. In a microsegmented network, NGFWs can be used with VLANs to enforce security policies and filter network traffic (see figure).
Figure 2: Industrial control system (ICS) microsegmentation
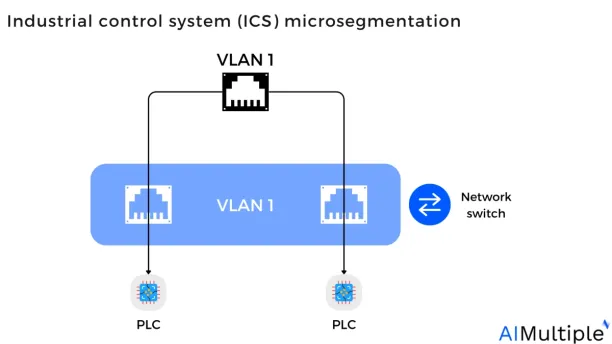
Note: With the PLC-level integrated microsegmentation the organization can expand VLAN capabilities beyond layer 2 communication to layer 3 (routing) and layer 7 (application visibility), allowing for traffic inspection.
Read more: OT network segmentation.
4. Tier segmentation
Tier segmentation protects separate tiers or levels of an application stack, such as the web, application, and database tiers, to prevent intruders from traveling laterally inside the application stack.
Web tier microsegmentation example: Administrators can create a distinct zone for the web server tier to perform granular security policies. Administrators can place the web server layer on a distinct network, such as a VLAN. All traffic flowing in and out of the VLAN—all traffic that enters and departs the data center—will pass via a next-generation firewall that is located inside the web tier. The next-generation firewall (e.g. web application firewall WAF) then can be configured with a software-defined networking (SDN) solution to filter outside traffic.
Additionally, to prohibit servers in the web server tier from connecting to each other, administrators can use a standard rule such as a distributed firewall (DFW) to open a port or restrict communication inside the tier.
Figure 3: Web application tier microsegmentation
Source: OWASP3
5. IoT device segmentation
Microsegmentation can help isolate existing network devices from new device connections by assigning them to an appropriate security profile using a zero-trust policy at both the ethernet (LAN) and internet layers.
Example: Companies that use an identity management and access control system can receive notifications for each new device added to their network. With microsegmentation companies can create distinct zones based on the device profiles during the onboarding. Network administrators can examine data from the device’s fingerprint to determine its identity and potential purpose. Then assign the device to an appropriate security zone. For example,
- Guests and visitors’ devices can be directed to the secure gateway.
- Devices that cannot be onboarded are placed in isolation zones where devices are only allowed to utilize the internet with restricted access.
- Unidentified and suspicious devices can be put into the “denylist” zone where they may not even receive an IP address.
Figure 4: Allowing virtual private cloud (VPC) access for a special VPC-Id: abc12345

Source: Tecracer4
6. Application segmentation
Application segmentation secures particular applications by establishing security policies that restrict access to specific application resources such as databases, APIs, and web servers.
Example: The whitelist constraints in the figure allow connections between Kubernetes services (all nodes) and require a specific protocol to be utilized. For example, rule 10002 necessitates the redis application protocol to connect “node.js demo nods” and “redis demo nods”.
Figure 5: Layer 7 application rules

Source: SUSE5
7. Container segmentation
With microsegmentation organizations can segment containers or groups of containers in a containerized environment, decreasing the attack surface and preventing attackers from moving laterally.
Administrators can use technologies such as Docker or Kubernetes to keep containers separate from the host system and other containers on the same network during container isolation. This stops containers from accessing resources outside their intended scope. There are three methods for isolating the contained application: Linux, Sandbox, and Virtual Machines. In this context, we’ll examine an example of Linux containers.
Linux containerization: Linux containers, such as Docker, employ control groups (cgroups), seccomp filters, and kernel namespaces to separate containers. Cgroups allow users to set resource use constraints on a group of processes. For example, cgroups can limit the use of various resources such as memory, network, and individual CPUs. Seccomp enables users to filter all system operations generated by a process. This filtering uses the kernel namespacing approach, which allows functions within a container to have an isolated view of the system.
Example: In the figure, the namespace provides a layer of separation for containers by providing them access to what appears to be their own Linux filesystem. Respectively,
- The mount (mnt) command asks the operating system to create a file system accessible from a certain place (the mount point).
- A UTS (UNIX Time-Sharing System) namespace is a Linux kernel that isolates two system identifiers: the hostname and the (network information service (NIS) domain name.
- Inter-process communication (IPC) is a method that enables processes to interact with one another and coordinate their operations.
Figure 6: Example of a filtering with kernel namespacing

Source: opensouce6
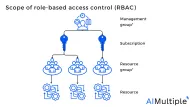
8. Role-based access control (RBAC)
Role-based access control (RBAC) is the process of providing permissions to employees based on their role within a company. When utilizing RBAC for microsegmentation, companies may examine users’ requirements and assign them to roles based on related duties. Companies then can assign each user one or more roles to decide which employee will receive access to network applications, data, and authorizations.
Example: Allianz, a multinational financial services insurance company, can manage sensitive personal and financial information and support regulatory compliance with RBAC by assigning roles such as:
Role: Insurance underwriter
Responsibilities: Collect, review, and analyze an applicant’s relevant history and records. Determine the level of risk for insuring or lending.
Permissions: Access to client accounts and transaction history at their branch.
Role: Loan officer
Responsibilities: Assess loan applications, analyzing creditworthiness, income documentation, and collateral.
Permissions: Access to credit ratings, financial records, and loan management systems.
Read more: RBAC use cases, RBAC examples.
9. DevOps segmentation
DevOps environments are prone to frequent changes, short deployment cycles, and high levels of automation. This can expose them to security dangers since changes in the environment might bring new vulnerabilities or misconfigurations. Microsegmentation may be used to protect DevOps environments by generating separate network segments for each stage of the software development process.
Example: Different segments can be built for software testing and development environments (e.g. Azure Region 1, Azure Region 2…). Administrators can disable SSH port 22, RDP port 3389, and other high-risk ports from the internet to protect the solution against security breaches across all virtual networks in the company.
Figure 7: Multiple DevOps virtual networks across multiple network segments

Source: Azure7
10. Virtual Desktop Infrastructure (VDI)
Virtual Desktop Infrastructure (VDI) is a microsegmentation technology that allows desktop environments to be hosted on a single server or in the cloud. With VDI users can access these virtual desktop settings remotely across the network using their laptops.
Example: Organizations can use either persistent or nonpersistent VDI’s:
- Persistent VDI provides users with a virtual desktop from the system’s resource pool. The user may personalize the desktop, install applications, make file modifications, and do everything else that a standard desktop allows, and these changes are stored, hence when the user signs in, they will be sent to the same desktop.
- Nonpersistent VDI gives a user a standard desktop on each login. The user’s modifications will only be available during that session; after the user exits, the VM will not be utilized again. Nonpersistent VDIs are often used for task employees who do not require customization in their workspace.
11. Adhering to compliance
Numerous companies are subject to regulatory regulations regarding data privacy, data protection, and network security. Microsegmentation can assist enterprises in achieving these compliance standards by giving them more control over network traffic.
For example, a microsegmentation policy can be designed to restrict access to sensitive data or apps to authorized employees while restricting all other traffic. This may assist companies in demonstrating regulatory compliance.
Read more: Network segmentation vs microsegmentation.
Who should use microsegmentation?
Any organization may need to leverage microsegmnetation in its process. In this section, we group some of the important categories that we recommend using microsegmentation.
Large-scale: Microsegmentation is suggested for enterprises with complicated and resource-intensive networks since it provides highly granular, application-level security configurations. Thus. enterprises with thousands of endpoints may isolate different parts of the network, such as web servers, database servers, and application servers with microsegmentation.
Cloud-native: Organizations that employ several software, cloud, and SaaS platforms should use microsegmentation solutions. These enterprises maintain most of their workload across the cloud and are more vulnerable to server-to-server breaches.
Healthcare: Healthcare providers must take precautions to protect sensitive patient data, therefore they may opt to carve aside high-security portions of their network for medical record storage.
Retail: Payment card industry (PCI) network segmentation is critical for retailers, and it entails rigorously restricting access to network components that process cardholder data.
Government: Federal agencies will be obligated to segregate their computer systems down to the level of individual applications, limiting the scope of cyber assaults. Thus, microsegmentation should be used by government organizations to segregate systems that contain sensitive data including “confidential” “secret” or “top secret” information.
For guidance on choosing the right tool or service, check out our data-driven sources: network security policy management (NSPM) tools and incident response tools.
Further reading
- Top 10 Microsegmentation Tools
- Role-based access control (RBAC)
- Network Segmentation: 6 Benefits & 8 Best Practices
- 80+ Network Security Statistics
- Network Security Policy Management Solutions (NSPM)
- Top 10 SDP Software Based on 4,000+ Reviews
- Top 10 Network Security Audit Tools Based on 4,000 Reviews
AIMultiple can assist your organization in finding the right vendor.
External Links
- 1. ”Most important reasons for companies to adopt micro-segmentation worldwide in 2021“. Statista. March 31, 2023. Retrieved May 5, 2024.
- 2. ”AWS Blog“. Tecracer. 2022. Retrieved May 10, 2024.
- 3. ”OWASP Network Segmentation“. OWASP. 2024. Retrieved May 5, 2024.
- 4. ”AWS Blog“. Tecracer. 2022. Retrieved May 10, 2024.
- 5. ”Container Segmentation Strategies and Patterns“. SUSE. March 12, 2019. Retrieved May 5, 2024.
- 6. ”4 Linux technologies fundamental to containers“. opensource. September 2, 2021. Retrieved May 5, 2024.
- 7. ”Secure and govern workloads with network-level segmentation“. Azure. 2024. Retrieved May 6, 2024.

Cem is the principal analyst at AIMultiple since 2017. AIMultiple informs hundreds of thousands of businesses (as per Similarweb) including 60% of Fortune 500 every month.
Cem's work has been cited by leading global publications including Business Insider, Forbes, Washington Post, global firms like Deloitte, HPE, NGOs like World Economic Forum and supranational organizations like European Commission. You can see more reputable companies and media that referenced AIMultiple.
Throughout his career, Cem served as a tech consultant, tech buyer and tech entrepreneur. He advised enterprises on their technology decisions at McKinsey & Company and Altman Solon for more than a decade. He also published a McKinsey report on digitalization.
He led technology strategy and procurement of a telco while reporting to the CEO. He has also led commercial growth of deep tech company Hypatos that reached a 7 digit annual recurring revenue and a 9 digit valuation from 0 within 2 years. Cem's work in Hypatos was covered by leading technology publications like TechCrunch and Business Insider.
Cem regularly speaks at international technology conferences. He graduated from Bogazici University as a computer engineer and holds an MBA from Columbia Business School.
Sources:
AIMultiple.com Traffic Analytics, Ranking & Audience, Similarweb.
Why Microsoft, IBM, and Google Are Ramping up Efforts on AI Ethics, Business Insider.
Microsoft invests $1 billion in OpenAI to pursue artificial intelligence that’s smarter than we are, Washington Post.
Data management barriers to AI success, Deloitte.
Empowering AI Leadership: AI C-Suite Toolkit, World Economic Forum.
Science, Research and Innovation Performance of the EU, European Commission.
Public-sector digitization: The trillion-dollar challenge, McKinsey & Company.
Hypatos gets $11.8M for a deep learning approach to document processing, TechCrunch.
We got an exclusive look at the pitch deck AI startup Hypatos used to raise $11 million, Business Insider.
To stay up-to-date on B2B tech & accelerate your enterprise:
Follow on
Comments
Your email address will not be published. All fields are required.